Ransomware: How it happens, the effects of data hostage and how to prevent it from happening to you.
Ransomware attacks are quickly becoming a serious threat that businesses MUST consider. Ransomware doesn’t discriminate, these cyber criminals target small mom and pop shops to enterprise level organizations… S T O P believing it won’t happen to you! If Delta Airlines, hospitals, and Embassies can fall victim, so can you.
The average ransomware attack yielded $1,077 last year representing a 266% spike from a year earlier. An IBM Security study from December 2016 found that over half of the businesses surveyed said they had already paid over $10,000 in ransom.
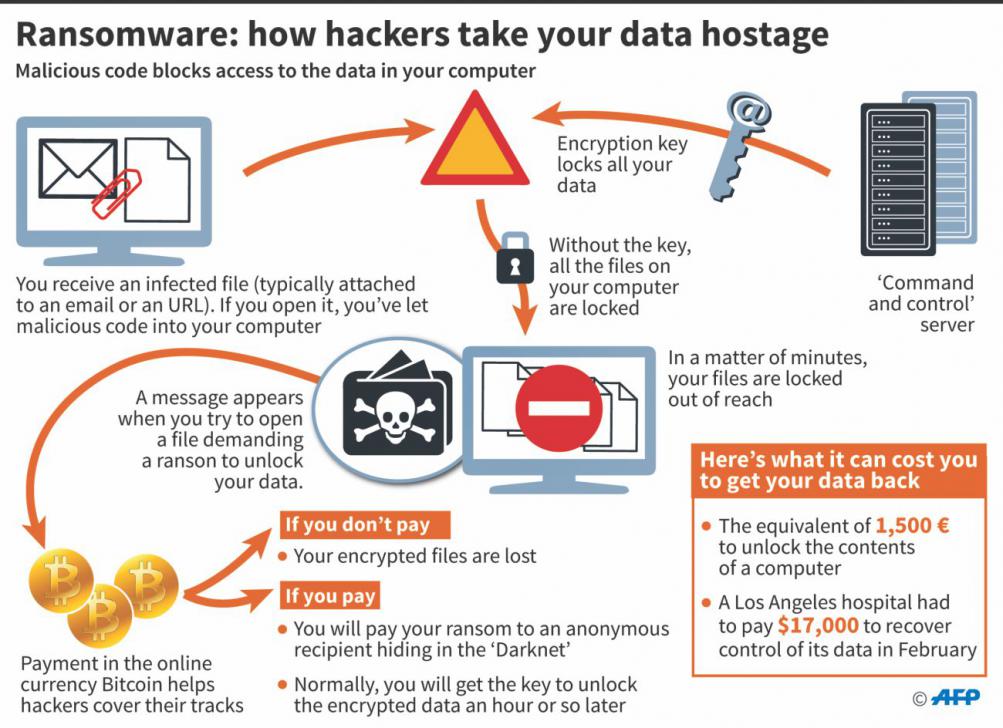
Attacks come primarily through email phishing or compromised websites. The New York Times, BBC and AOL inadvertently ran malicious ads that attempted to hijack the computers of visitors and demand a ransom.
Case Studies
- Hollywood Presbyterian Medical Center paid $16,700 for access back to their data after ransomware infection.
- in 2016, a ransomware attack forced a county in Indiana to pay a $21,000 ransom, as well as invest more than $200,000 in beefing up its department and security.
- An unidentified hacker took home $28,000 after Los Angeles Valley College (LAVC) was hit with a ransomware attack and paid the fee for fear of permanently losing data on school computers.
Prevention and Remediation of Ransomware
File and Directory Monitoring:
- By using the built in Windows service you can be alerted of changes to file/folder to try and prevent the spread of infection. You can also setup blocking of certain file extensions such as .zip, .doc, .rtf
Backup and Disaster Recovery:
- You need a local backup for quick file restore and testing as well as an offsite backup for disaster recovery, either natural or man made. Some ransomware attackers search out local backup systems and network shares to encrypt so that a cloud based backup becomes the only restore method.
Employee Training:
- KnowBe4 offers security awareness training for companies. With awareness training the number of workers clicking on phishing attacks drop from 15.9 percent to just 1.2 percent in some companies.
Patch and Block:
- Update Windows and associated programs as well as third party programs such as QuickBooks, internet browsers, etc. You can also white-list approved applications since the lists won’t let your computer install anything that’s not already approved.
What To Do If You Get Infected with Ransomware
- Immediately shut down network operations to prevent the infection from spreading
- Disconnect infected systems from the network, also disable Wi-Fi and Bluetooth on machines to prevent the malware from spreading to other machines via those methods
- Contact CCSI (817) 459-4000