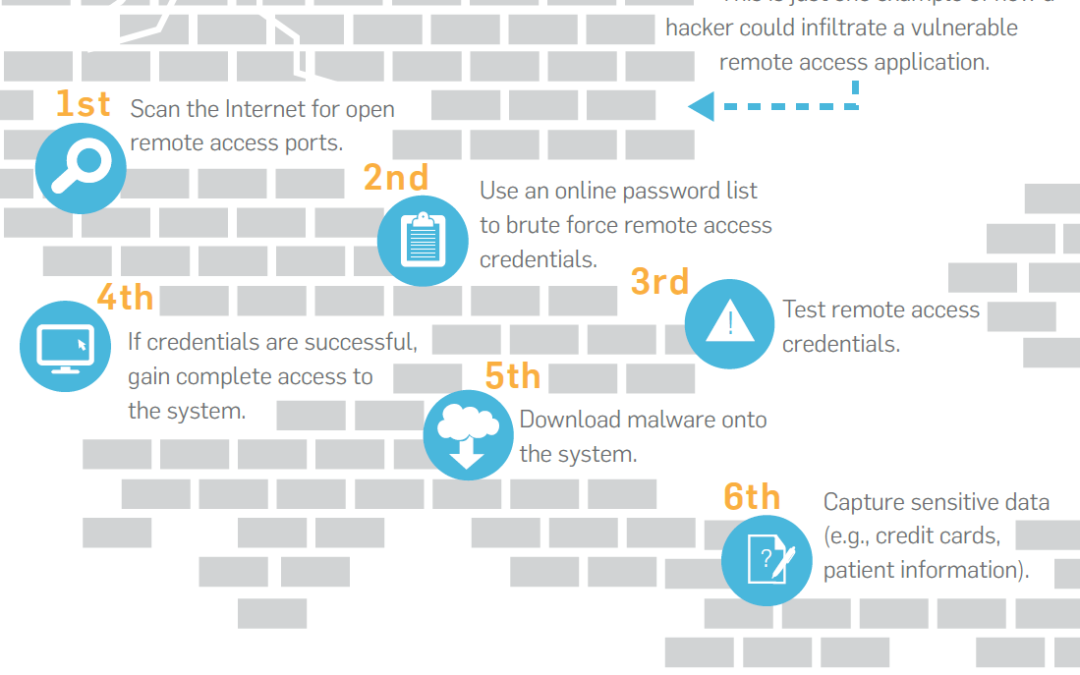
Remote desktop access (RDP) is one of the most common and easiest ways to access computers and servers on your network. For businesses with remote users, this is a common practice, but most are unaware of the security risks this opens them up to. Even those who are aware of the risks often still choose the ease and cost savings that RDP provides. So, what is RDP and what makes it such a security risk? Simply put, RDP is a tool to remotely connect and control a PC or server on a network. By default, RDP uses the port 3389. Leaving this port open means that attackers can find and then launch a ‘brute force’ attack. Sending 1000s of random usernames and passwords at the server until they are in. Once they are on the system there is no end to the damage they can cause. From viruses to Ransomware, costing tens of thousands of dollars in damage if not more. Even if attackers do not make their way in, you and your business can still feel the impact. These brute force attacks hit your server with thousands of failed login attempts which can slow performance and productivity to a crawl. While there are some workarounds to better secure yourself against these kinds of attacks; changing port numbers or using third party software to detect and mitigate the effects of brute force attacks. We at CCSI believe the best option is to remove the problem all together.
CCSI has been migrating it’s clients to the more secure and more reliable use of VPN’s. VPN (or Virtual Private Network) creates an encrypted ‘tunnel’ into the network making it so that RDP ports will no longer need to be opened on the firewall. No open ports means there is nothing for attackers to attempt to force their way in to.