by Mellissa Lologo | Dec 12, 2017 | IT Services |
Ransomware: How it happens, the effects of data hostage and how to prevent it from happening to you.
Ransomware attacks are quickly becoming a serious threat that businesses MUST consider. Ransomware doesn’t discriminate, these cyber criminals target small mom and pop shops to enterprise level organizations… S T O P believing it won’t happen to you! If Delta Airlines, hospitals, and Embassies can fall victim, so can you.
The average ransomware attack yielded $1,077 last year representing a 266% spike from a year earlier. An IBM Security study from December 2016 found that over half of the businesses surveyed said they had already paid over $10,000 in ransom.
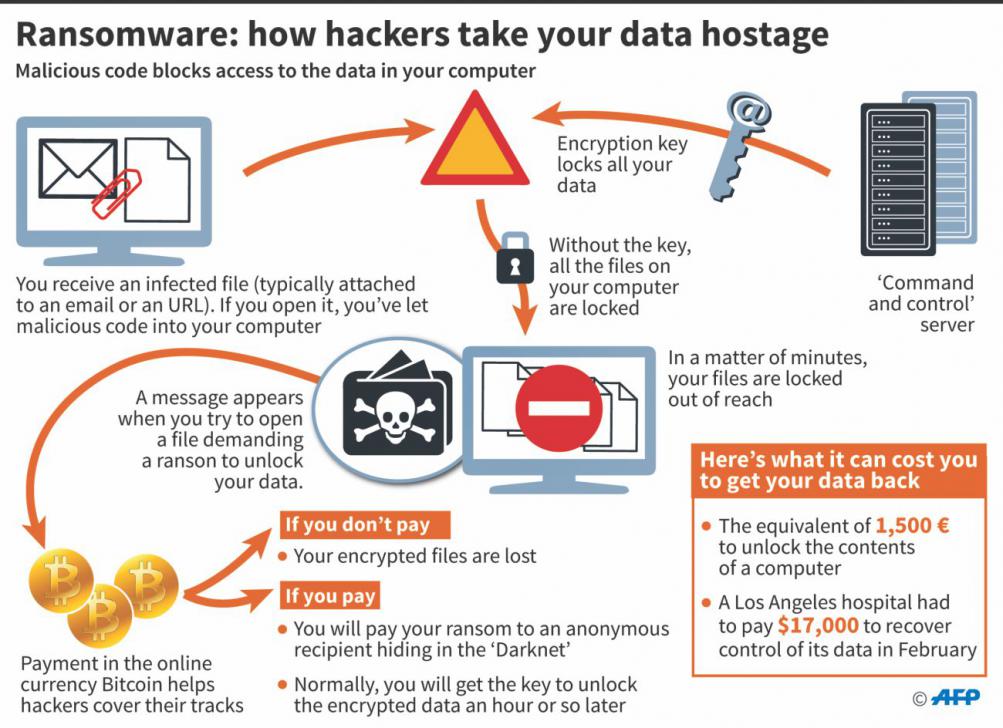
Attacks come primarily through email phishing or compromised websites. The New York Times, BBC and AOL inadvertently ran malicious ads that attempted to hijack the computers of visitors and demand a ransom.
Case Studies
- Hollywood Presbyterian Medical Center paid $16,700 for access back to their data after ransomware infection.
- in 2016, a ransomware attack forced a county in Indiana to pay a $21,000 ransom, as well as invest more than $200,000 in beefing up its department and security.
- An unidentified hacker took home $28,000 after Los Angeles Valley College (LAVC) was hit with a ransomware attack and paid the fee for fear of permanently losing data on school computers.
Prevention and Remediation of Ransomware

File and Directory Monitoring:
- By using the built in Windows service you can be alerted of changes to file/folder to try and prevent the spread of infection. You can also setup blocking of certain file extensions such as .zip, .doc, .rtf
Backup and Disaster Recovery:
- You need a local backup for quick file restore and testing as well as an offsite backup for disaster recovery, either natural or man made. Some ransomware attackers search out local backup systems and network shares to encrypt so that a cloud based backup becomes the only restore method.
Employee Training:
- KnowBe4 offers security awareness training for companies. With awareness training the number of workers clicking on phishing attacks drop from 15.9 percent to just 1.2 percent in some companies.
Patch and Block:
- Update Windows and associated programs as well as third party programs such as QuickBooks, internet browsers, etc. You can also white-list approved applications since the lists won’t let your computer install anything that’s not already approved.
What To Do If You Get Infected with Ransomware
- Immediately shut down network operations to prevent the infection from spreading
- Disconnect infected systems from the network, also disable Wi-Fi and Bluetooth on machines to prevent the malware from spreading to other machines via those methods
- Contact CCSI (817) 459-4000


by Mellissa Lologo | Dec 11, 2017 | IT Services |
What is Bad Rabbit?
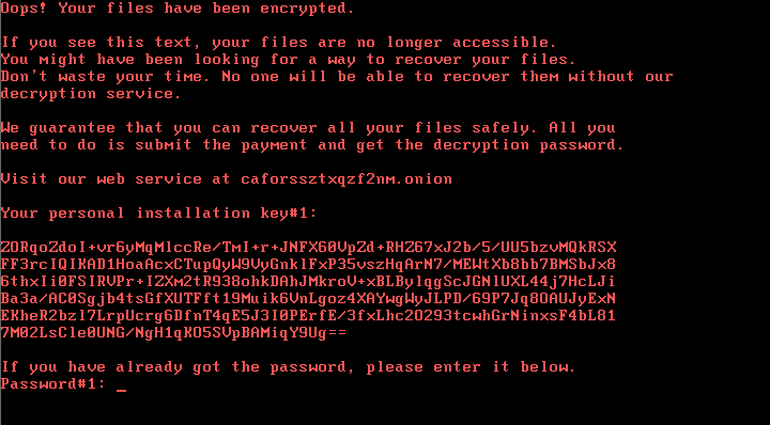
Bad Rabbit is malicious software that infects a PC and restricts user access to the infected computer until a ransom is paid to unlock it. On October 24th notifications of mass attacks with ransomware called Bad Rabbit ignited. It targets organizations and consumers, mostly in Russia but there have also been reports of victims in Ukraine. Here’s what a ransom message looks like for the unlucky victims:
How is Bad Rabbit Distributed?
The ransomware dropper is distributed with the help of “drive by attacks”. While the target is visiting a legitimate website, a malware dropper is being downloaded from the threat actor’s infrastructure. No exploits are used, so the victim would have to manually execute the malware dropper, which pretends to be an Adobe Flash installer. Further analysis confirmed that Bad Rabbit uses the EternalRomance exploit as an infection vector to spread within corporate networks. The same exploit was used in the ExPetr. There are a number of compromised websites, majority being major news or media websites.
Who Does it Target?
Most of the targets are located in Russia. Similar but fewer attacks have also been seen in other countries – Ukraine, Turkey and Germany. Overall, there are almost 200 targets, according to the KSN statistics.
How is Bad Rabbit Different to ExPetr? Or is it the Same?
Observations suggest that this been a targeted attack against corporate networks, using methods similar to those used during the ExPetr attack. What’s more, the code analysis showed a notable similarity between the code of ExPetr and Bad Rabbit binaries.
Decryption Opportunity Assesment
Unlike ExPetr, the evidence suggests that Bad Rabbit is not intended as a wiper. The threat actors behind ExPetr were technically unable to decrypt MFT that was encrypted with the GoldenEye component. In the case of Bad Rabbit, however, the malware algorithm suggests that the threat actors have the technical means to decrypt the password necessary for disk decryption.
The data shown on the screen of an infected machine as “personal installation key#1” is an encrypted by RSA-2048 and base64-encoded binary structure that contains the following information gathered from the infected system:
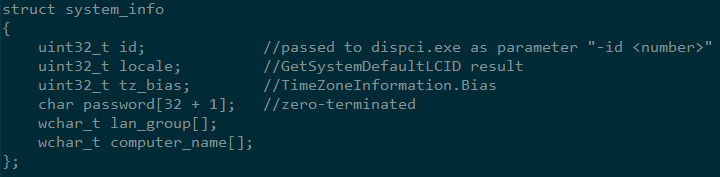
The threat actors can use their own private RSA key to decrypt this structure. After decryption they can send this information to the victim.
As part of the analysis, the password generated by the malware during a debugging session was extracted. Then attempted to enter this password when the system was locked after reboot. The password indeed worked and the boot-up process continued.
Unfortunately, have to conclude that at this point there’s no way to decrypt disk and victim files without the threat actor’s RSA-2048 private key. The symmetric encryption keys are securely generated on the ransomware side which makes attempts to guess the keys unfeasible in practice.
However, there is a flaw in the code of dispci.exe: the malware doesn’t wipe the generated password from the memory, which means that there is a slim chance to extract it before the dispci.exe process terminates. In the picture below, note that while the variable dc_pass (which will be passed to the driver) is securely erased after use, that’s not the case for the variable rand_str which holds the original copy of the password.
File Encryption
the trojan uses a common file encryption scheme. It generates a random 32-bytes-length string and uses it in the key derivation algorithm. Unfortunately, the trojan uses the CryptGenRandom function when generating this string.
Ransom note creation routine
An interesting fact is that the trojan cannot encrypt files which have a Read-only attribute.
File Recovery Possibility
Bad Rabbit does not delete shadow copies after encrypting the victim’s files. Meaning that if the shadow copies had been enabled prior to infection and if the full disk encryption did not occur, then the victim can restore the original versions of the encrypted files with the standard Windows mechanism or third party utilities.
Manually Remove Bad Rabbit Ransomware
1. First of all to Remove Bad Rabbit Virus , check all the shortcuts of browser on the desktop, taskbar and Start menu. Right click on the shortcut and completely change its properties
2. Investigate list of installed programs and uninstall the unknown recently downloaded programs directly
3. Then, Open Task Manager and close the processes that relates to the Bad Rabbit Ransomware in its description. Completely discover all directories in which these processes start. Navigate for a random or different file name
4. Inspect all the Windows Services. Press Win+R type in: services.msc and then Press OK
5. Disable services with complete random names and it contains Bad Rabbit Virus in the name or description
6. Once done with it press Win+R and type in taskchd.msc and after that press Ok for opening Windows Task
Scheduler. In this section, delete a task that are related to the Bad Rabbit Malware and then disable unknown tasks having the random names
7. Clear Windows Registry from Bad Rabbit Virus and press Win+R, type in: regedit.exe and then press Ok. Find it and delete all the keys/values contained in Bad Rabbit Ransomware
8. Remove Bad Rabbit Virus from all the browsers like Chrome, Explorer, Firefox, etc and in case any step is skipped the virus can come back in the system.
Reccomendations
Kaspersky Lab corporate customers are advised to:
- Make sure that all protection mechanisms are activated as recommended; and that KSN and System Watcher components (which are enabled by default) are not disabled.
- Update the antivirus databases immediately.
Additional Precautions:
- Restricting execution of files with the paths c:\windows\infpub.datand C:\Windows\cscc.dat in Kaspersky Endpoint Security.
- Configuring and enabling Default Deny mode in the Application Startup Control component of Kaspersky Endpoint Security to ensure and enforce proactive defense against this and other attacks.








