by Mellissa Lologo | Dec 12, 2017 | IT Services |
Ransomware: How it happens, the effects of data hostage and how to prevent it from happening to you.
Ransomware attacks are quickly becoming a serious threat that businesses MUST consider. Ransomware doesn’t discriminate, these cyber criminals target small mom and pop shops to enterprise level organizations… S T O P believing it won’t happen to you! If Delta Airlines, hospitals, and Embassies can fall victim, so can you.
The average ransomware attack yielded $1,077 last year representing a 266% spike from a year earlier. An IBM Security study from December 2016 found that over half of the businesses surveyed said they had already paid over $10,000 in ransom.
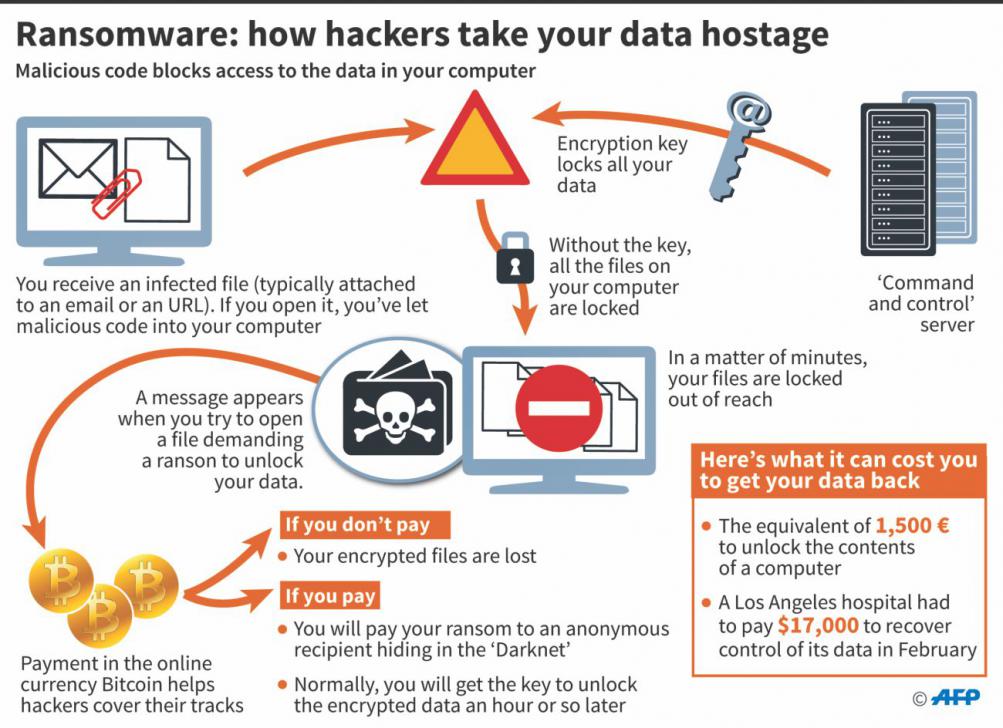
Attacks come primarily through email phishing or compromised websites. The New York Times, BBC and AOL inadvertently ran malicious ads that attempted to hijack the computers of visitors and demand a ransom.
Case Studies
- Hollywood Presbyterian Medical Center paid $16,700 for access back to their data after ransomware infection.
- in 2016, a ransomware attack forced a county in Indiana to pay a $21,000 ransom, as well as invest more than $200,000 in beefing up its department and security.
- An unidentified hacker took home $28,000 after Los Angeles Valley College (LAVC) was hit with a ransomware attack and paid the fee for fear of permanently losing data on school computers.
Prevention and Remediation of Ransomware

File and Directory Monitoring:
- By using the built in Windows service you can be alerted of changes to file/folder to try and prevent the spread of infection. You can also setup blocking of certain file extensions such as .zip, .doc, .rtf
Backup and Disaster Recovery:
- You need a local backup for quick file restore and testing as well as an offsite backup for disaster recovery, either natural or man made. Some ransomware attackers search out local backup systems and network shares to encrypt so that a cloud based backup becomes the only restore method.
Employee Training:
- KnowBe4 offers security awareness training for companies. With awareness training the number of workers clicking on phishing attacks drop from 15.9 percent to just 1.2 percent in some companies.
Patch and Block:
- Update Windows and associated programs as well as third party programs such as QuickBooks, internet browsers, etc. You can also white-list approved applications since the lists won’t let your computer install anything that’s not already approved.
What To Do If You Get Infected with Ransomware
- Immediately shut down network operations to prevent the infection from spreading
- Disconnect infected systems from the network, also disable Wi-Fi and Bluetooth on machines to prevent the malware from spreading to other machines via those methods
- Contact CCSI (817) 459-4000


by Mellissa Lologo | Dec 11, 2017 | IT Services |
What is Bad Rabbit?
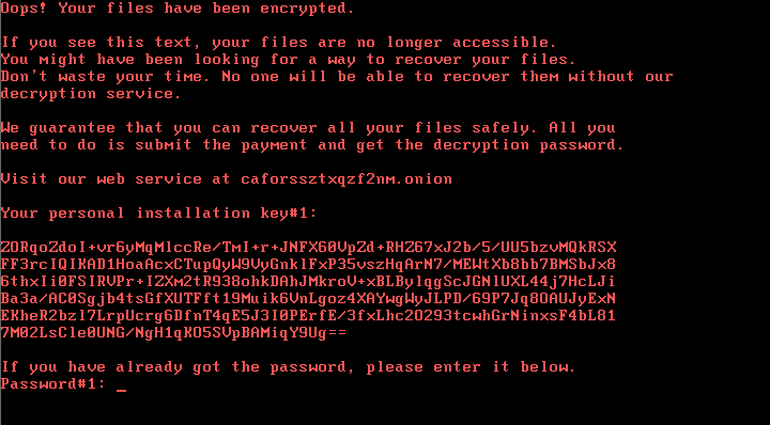
Bad Rabbit is malicious software that infects a PC and restricts user access to the infected computer until a ransom is paid to unlock it. On October 24th notifications of mass attacks with ransomware called Bad Rabbit ignited. It targets organizations and consumers, mostly in Russia but there have also been reports of victims in Ukraine. Here’s what a ransom message looks like for the unlucky victims:
How is Bad Rabbit Distributed?
The ransomware dropper is distributed with the help of “drive by attacks”. While the target is visiting a legitimate website, a malware dropper is being downloaded from the threat actor’s infrastructure. No exploits are used, so the victim would have to manually execute the malware dropper, which pretends to be an Adobe Flash installer. Further analysis confirmed that Bad Rabbit uses the EternalRomance exploit as an infection vector to spread within corporate networks. The same exploit was used in the ExPetr. There are a number of compromised websites, majority being major news or media websites.
Who Does it Target?
Most of the targets are located in Russia. Similar but fewer attacks have also been seen in other countries – Ukraine, Turkey and Germany. Overall, there are almost 200 targets, according to the KSN statistics.
How is Bad Rabbit Different to ExPetr? Or is it the Same?
Observations suggest that this been a targeted attack against corporate networks, using methods similar to those used during the ExPetr attack. What’s more, the code analysis showed a notable similarity between the code of ExPetr and Bad Rabbit binaries.
Decryption Opportunity Assesment
Unlike ExPetr, the evidence suggests that Bad Rabbit is not intended as a wiper. The threat actors behind ExPetr were technically unable to decrypt MFT that was encrypted with the GoldenEye component. In the case of Bad Rabbit, however, the malware algorithm suggests that the threat actors have the technical means to decrypt the password necessary for disk decryption.
The data shown on the screen of an infected machine as “personal installation key#1” is an encrypted by RSA-2048 and base64-encoded binary structure that contains the following information gathered from the infected system:
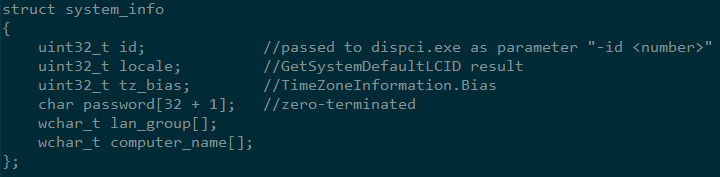
The threat actors can use their own private RSA key to decrypt this structure. After decryption they can send this information to the victim.
As part of the analysis, the password generated by the malware during a debugging session was extracted. Then attempted to enter this password when the system was locked after reboot. The password indeed worked and the boot-up process continued.
Unfortunately, have to conclude that at this point there’s no way to decrypt disk and victim files without the threat actor’s RSA-2048 private key. The symmetric encryption keys are securely generated on the ransomware side which makes attempts to guess the keys unfeasible in practice.
However, there is a flaw in the code of dispci.exe: the malware doesn’t wipe the generated password from the memory, which means that there is a slim chance to extract it before the dispci.exe process terminates. In the picture below, note that while the variable dc_pass (which will be passed to the driver) is securely erased after use, that’s not the case for the variable rand_str which holds the original copy of the password.
File Encryption
the trojan uses a common file encryption scheme. It generates a random 32-bytes-length string and uses it in the key derivation algorithm. Unfortunately, the trojan uses the CryptGenRandom function when generating this string.
Ransom note creation routine
An interesting fact is that the trojan cannot encrypt files which have a Read-only attribute.
File Recovery Possibility
Bad Rabbit does not delete shadow copies after encrypting the victim’s files. Meaning that if the shadow copies had been enabled prior to infection and if the full disk encryption did not occur, then the victim can restore the original versions of the encrypted files with the standard Windows mechanism or third party utilities.
Manually Remove Bad Rabbit Ransomware
1. First of all to Remove Bad Rabbit Virus , check all the shortcuts of browser on the desktop, taskbar and Start menu. Right click on the shortcut and completely change its properties
2. Investigate list of installed programs and uninstall the unknown recently downloaded programs directly
3. Then, Open Task Manager and close the processes that relates to the Bad Rabbit Ransomware in its description. Completely discover all directories in which these processes start. Navigate for a random or different file name
4. Inspect all the Windows Services. Press Win+R type in: services.msc and then Press OK
5. Disable services with complete random names and it contains Bad Rabbit Virus in the name or description
6. Once done with it press Win+R and type in taskchd.msc and after that press Ok for opening Windows Task
Scheduler. In this section, delete a task that are related to the Bad Rabbit Malware and then disable unknown tasks having the random names
7. Clear Windows Registry from Bad Rabbit Virus and press Win+R, type in: regedit.exe and then press Ok. Find it and delete all the keys/values contained in Bad Rabbit Ransomware
8. Remove Bad Rabbit Virus from all the browsers like Chrome, Explorer, Firefox, etc and in case any step is skipped the virus can come back in the system.
Reccomendations
Kaspersky Lab corporate customers are advised to:
- Make sure that all protection mechanisms are activated as recommended; and that KSN and System Watcher components (which are enabled by default) are not disabled.
- Update the antivirus databases immediately.
Additional Precautions:
- Restricting execution of files with the paths c:\windows\infpub.datand C:\Windows\cscc.dat in Kaspersky Endpoint Security.
- Configuring and enabling Default Deny mode in the Application Startup Control component of Kaspersky Endpoint Security to ensure and enforce proactive defense against this and other attacks.

by Mellissa Lologo | Oct 27, 2017 | IT Services |
What is WiFi Security?
 Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are wired equivalent Privacy (WEP) and WiFi Protected Access (WPA).
Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are wired equivalent Privacy (WEP) and WiFi Protected Access (WPA).
Does This Effect Me?
YES! E-V-E-R-Y-O-N-E is at Risk! Consumer Reports latest article alongside numerous tech world and major news outlets all report how serious the threat is and expose the vulnerability that anyone with a computer, laptop, smartphone, tablet…etc. and router are ALL exposed, sitting ducks, with a plethora of private information out there for the criminals to grab. A fix is eminent and in the works but with the hot topic now on the airwaves, any hacker who didn’t know of the flaw before is utilizing every available resource now to crack the KRACK before it can no longer be hacked.
How?
Every WiFi connection around the world is officially vulnerable to hackers. This is the first security flaw found in modern technologies that are supposed to SECURE WiFi networks since 2002 and has been named “KRACK Attack” short for, Key Reinstallation AttaCK, by Mathy Vanhoef, a security expert at Belgian University, KU- L euven. The discovery of the weakness in the wireless security protocol, WPA2, that is used to protect the vast majority of WiFi connections shows how hackers are able to inject PC viruses into internet networks, read peoples passwords, credit card numbers, eavesdrop on private conversations, read emails and view photographs sent over the web. Full disclosure and view of your every click, purchase and move throughout your personal or businesses entire network. Connecting to a secure network requires a four-way “handshake” between a device and a router to ensure that nobody else can decrypt the traffic. Mathy Vanhoef found a way to install a new “key” used to encrypt the communications onto the network, allowing a hacker to gain access to the data.
euven. The discovery of the weakness in the wireless security protocol, WPA2, that is used to protect the vast majority of WiFi connections shows how hackers are able to inject PC viruses into internet networks, read peoples passwords, credit card numbers, eavesdrop on private conversations, read emails and view photographs sent over the web. Full disclosure and view of your every click, purchase and move throughout your personal or businesses entire network. Connecting to a secure network requires a four-way “handshake” between a device and a router to ensure that nobody else can decrypt the traffic. Mathy Vanhoef found a way to install a new “key” used to encrypt the communications onto the network, allowing a hacker to gain access to the data.
How is it Fixed?
The only way to “fix” the flaw would be to manually replace or patch every router in people’s homes and businesses. While the attack is not technically easy, tools will soon pop up allowing for criminals to carry out the attack. In the meantime, the most suggested method of protection for your network until this patch is created would be:
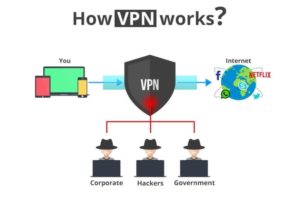
What Should You Do? Business Owners and Personal Protection Methods
Keep in mind that it may take some time for the manufacturer of your devices to come up with a security patch. In the meantime, there are extra steps you can take to help secure your devices.
If your business is paying someone to maintain and monitor your entire network, then they should be double-checking all devices to make sure they are patched to prevent this vulnerability. If you don’t have an agreement with an IT company like CCSI, this vulnerability could almost certainly affect your business.
Both Businesses and Home network users alike are encouraged to use a VPN (Virtual Private Network): VPN’s allow you to access the internet anonymously and protect your privacy online. Instead of your network directly connecting to your target site (let’s say Facebook), it connects you to a VPN server in the cloud which acts as your primary network and talks clearly to the target server on your behalf. The end server (Facebook) doesn’t know your real IP. Anybody who wants to watch you has to do it between your VPN server and your target server, your true network/IP is never exposed or put at risk.
Additionally, only using HTTPS-enabled websites means your web traffic will also be encrypted by SSL and may be safer from this vulnerability. HTTPS browsing adds an extra layer of security by using encryption via the website you are visiting.
Wi-Fi users should immediately update their Wi-Fi-enabled devices as soon as a software update is made available. Wi-Fi enabled devices are anything that connects to the Internet — from laptops, tablets, and smartphones to other smart devices such as wearables and home appliances.
by Mellissa Lologo | Oct 2, 2017 | IT Services |
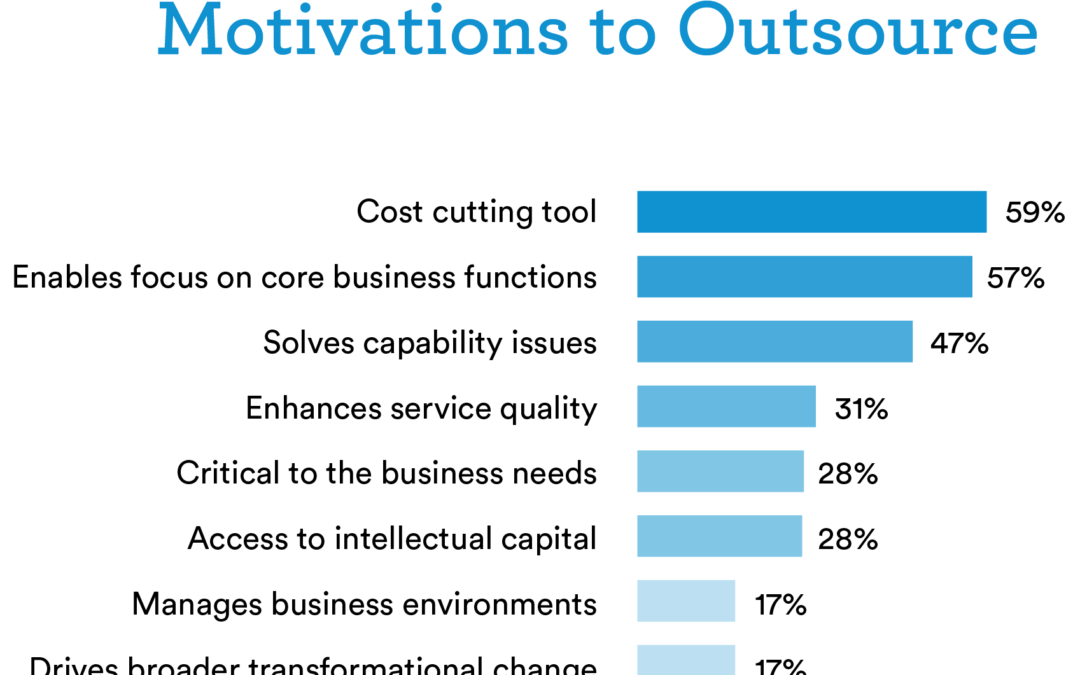
Although the above picture may look as if it is misplaced among the title and topic of this blog, I assure you, it serves a greater purpose. I wanted to show the magnitude and dominance that is the reality of technologies presence in today’s’ world, both business and pleasure. Businesses across every industry are discovering how today’s technologies help them achieve their objectives and propel them past their expectations. The pace which technology is advancing however, is unprecedented. While new technologies present powerful opportunities for business, they also bring challenges. For many businesses, those challenges add up to significant costs; the cost of hiring and training qualified workers, purchasing the infrastructure to support emerging technologies, and keeping systems up to date and secure. Rather than struggle to keep pace with technology many are turning to Managed IT service providers and outsourcing.
The benefits are clear. In 2014 the average percent of organizations who outsourced their IT was 30%. Within one year, that figure had nearly doubled. Managed IT services can cut IT costs by as much as 40 percent, all the while doubling operational efficiency. The following are just a few of the many benefits your organization could obtain through outsourcing your IT through a Managed IT service provider like CCSI.
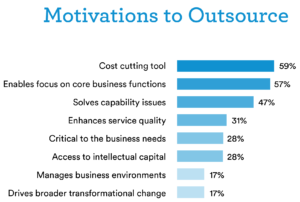
Immediate IT Outsourcing Benefits for Business
1.Control Over Your Budget
Outsourcing converts fixed IT costs into variable costs and allows effective budgeting. Basically, only pay for what you need when you need it. The amount of savings through outsourcing is often unrealized and the benefits huge.
2.Single Point of Service Outsourcing your IT through a single Managed IT Service vendor keeps the waters calm. Ideally you want to work with a partner, not a vendor. A managed IT provider who understands your industry and is familiar with your business from the inside out. Knowing the inner workings of your organization and not just the technology side, eliminating the need to obtain varying services through multiple vendors. When the comprehensiveness of your organization is cohesive, processes and projects are met with ease and any other issues are quickly extinguished. Basically, the less ducks in the pond the clearer the waters.
3. Reduced Costs in Labor
Every business owner knows, hiring and training is the largest expense and risk a business takes on. IT staff is no exception and VERY expensive. Temps aren’t a cost effective or practical solution for IT related projects either. Outsourcing your IT lets you focus your human resources where you need them most.
4. Greater Scalability IT shops spend months, sometimes years, deploying massive systems. Many businesses are finding it more effective to start small, move fast and expand as needed. Custom and modular approach to managed IT services makes it easy for organizations to scale up or down depending on demand, such as a retailer increasing capacity during the holiday season, or a startup experiencing sudden growth.
5.Qualified, Certified, Trained, EXPERIENCED
If you’re not IT trained, how do you assure an employee is qualified? Certifications like Microsoft Certified Systems Engineer (MCSE) are important, but so is experience.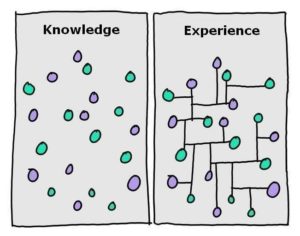
6. Experience Trumps Qualifications– EVERY TIME
Few problems are new for Managed IT services companies, they deal with them on a daily basis. Your biggest catastrophe is something they are well prepared for and fix on a regular. An in-house IT employee leads an isolated existence no matter how much they train and gain little experience doing maintenance and help desk tasks, and are paid a salary whether everything runs smoothly or not. Pay for the services you use, when you use them by a managed IT service provider who covers the entire IT spectrum from the hiccups to the hurricanes-literally.
7.Freeing up Existing IT Staff IT departments within organizations are mostly stretched thin as it is. Outsourcing for back-end functions or rapidly changing technologies allow organizations to dedicate their in-house tech experts to projects that advance their core objectives and promote innovation.
8. Gain a Competitive Edge and Increase Efficiency
Organizations that try to do all IT Services in-house themselves can have much higher research, development, and implementation time, all of which increase costs and are ultimately passed on to customers.
9. Keeping Pace with the Demands for IT Expertise The struggle to fill IT positions is worldwide, especially those positions in cyber security and mobile app development. Outsourcing these functions through a Managed IT service partner with technically skilled and specialized engineers in new and emerging technologies alleviates these pressures.
10. Quickly Implement New Technology
Managed IT service providers have the resources to start new projects immediately. Handling the same project in-house typically requires months to hire and train the right people, or overtime for the ones you’ve already got. IT companies bring years of experience for projects right from the beginning saving time and money as well as their knowledge of the most up to date products and solutions that have the capabilities to grow with your organization. Ultimately eliminating the need to implement new technology later down the road just to keep up. Future-proofing, quality managed IT service providers bring this aspect to the table and eliminate a host of future costs and time-consuming projects removing old hardware, implementing new…etc.
11. Stay Focused on Your Core Business
Businesses resources are typically limited to those that are industry related and your businesses manager probably isn’t an IT expert atop their existing job title. Outsourcing IT alleviates the time and stress robbed of your employees when a crisis emerges, big or small, and let them stay focused on their regular duties. Employees remain focused and efficient, managers are able to keep the business running making revenues. Everyone focused on the core business, not distracted by complex IT decisions.
12. Eliminate Unnecessary Risk and Shift the Burden of Compliance
In addition to regular audits, many organizations are required to meet standards with their IT initiatives. The Health Insurance Portability and Accountability Act, Family Educational Rights and Privacy Act, Payment Card Industry Data Security Standard and Sarbanes–Oxley Act, spell out rules regarding privacy, reporting and security in the healthcare, education, financial services and retail industries. Managed IT service providers assume and manage much of that risk for you, with specific industry knowledge, especially security and compliance issues. They generally are much better at deciding how to avoid risk in their areas of expertise — without placing that burden on in-house staff.
13. Level the Playing Field
Most small businesses can’t afford to match the in-house support services that larger companies maintain. Outsourcing can help small companies act “big” by giving them access to the similar technology, and expertise that large companies enjoy. An independent third party managed cost structure and economy of scale can give your company a competitive advantage.
14. Security, Safety and Compliance
Is your firewall up to date? Do you have a DMZ installed? Do you audit your Workstations and Servers? Has your company implemented PCI security standards and maintain those standards? Businesses now have more forms of payments than ever, such as, Credit/Debit cards, Pay-Pal, Electronic Checks, Gift Certificates, Wire Transfers, but with these transaction forms also require attentiveness. Outsourcing through a Managed IT Service company familiar with PCI Compliance standards can minimize the risks associated with maintaining client data, credit card numbers, sensitive competitive information. It also alleviates any hassle of software and hardware security monitoring and upgrades of the network. When that pop-up asking you if you’d like to upgrade to the newest version of a software arrives, you don’t have to worry if it’s a legitimate source asking and necessary update or not. Your Managed IT services provider keeps your network, data and all the necessary licensing agreements for software and hardware protected and up to date.

How to Know if Outsourcing Through a Managed IT Service Provider is Right for You:
- Constantly putting off new projects and facing a backlog of user requests are clear signs that it’s time to look into managed IT services, especially for a provider that delivers meaningful value.
- Before choosing a partner, organizations should clearly define their requirements and the improvements they expect to see. For example, they might want to introduce off-hours coverage for network technology or a mobile tracking platform that competitors are using.
- When meeting with prospective providers, operational teams should ask how they would achieve these goals. Beware of providers who talk only about their own characteristics — the toolsets they use, their processes, the quality of their engineering resources — instead of focusing on your organization’s goal.
- Another factor to consider is the provider’s breadth of experience. Many managed IT service providers focus on niche areas, but with the pace of change in technology, it’s important to work with a partner that can meet an organization’s needs now and in the future.

by Mellissa Lologo | Aug 24, 2017 | IT Services |
There are numerous challenges experienced by managed service providers when dealing with marketing and selling backup and disaster recovery planning services to existing and potential customers. IT experts understand the importance of this element for every business. However, communicating the significance of data backups and disaster recovery planning solutions to regular, non-techie people often proves difficult to convey. Let’s start off by differentiating between the two.
What is Backup?
Backups or backing up is a scheduled event in which tapes or disks are used for storing backup data either in the cloud or at another geographical location, like a co-location. This data is stored at a different location for the purpose of protecting it. Should you lose the files, either through disaster or simply by deleting them or overwriting them, you can just restore them from the saved copies that were backed up. But in order for this to work, the copies of your files must be updated regularly. Most backup software lets you schedule scans of your hard drive for new and changed files daily, weekly, or monthly, but my preferred option is to have the software continually (or at least, say, every 15 minutes) monitor your drive for changed or new files.
Cloud backup is a highly recommended and practiced process. The big plus being that the data is off your premises, and therefore not susceptible to local disasters. The downside is that they tie you to annual fees, and uploading and downloading backups is slower than loading local copies.
What is Disaster Recovery Planning?
Disaster Recovery Planning is a cloud based environment where all of your businesses vital information is stored, monitored and protected. This solution allows for entire networks and environments to be replicated at another location should it be necessary. For example- A flash flood hits your business, your server room is floating in 2 inches of flood water and your server with 5 years’ worth of your businesses files, customer information, finances…etc., is ruined. Since you’ve prepared for something potentially crippling, there is a full cloud environment with every operating piece, customer file, word document, custom made business application, marketing material- basically your entire business- is all right there, nothing lost, aside from the physical office space, and can be sent to any location needed. Pretty smart.
In summary, you can see the two are vastly different. Backups protect your files and business information back to a certain point and must be a frequently administered process in order to keep an entire business going should something happen. Disaster Recovery is for the entire cloud environment and can replicate and restore your data to any new location.
Why You May Not Know You Need It:
The difficulty in justifying the value of backups and disaster recovery technology to business owners can be attributed to a few things. Most managed service companies employ individuals based on their technical background. They’re geared more toward the technology, not marketing it, therefor, marketing skills to convince customers to implement backups or a disaster recovery plan, can prove challenging. Another contributing factor is the overwhelming potential cost of backups and disaster recovery planning, especially when a customer has a so called “data protection solution” software in place that they believe is protecting them.
Current Event- Delta Airlines, August 2016
August 2016, Delta Airlines has to cancel more than 1,300 flights, costing over $100 million, not because of bad weather, but because the company’s computer systems went down. If it can happen to a big corporation like Delta, don’t think it can’t happen to you. All technology, whether it’s a brand-new iMac, a spaceship, a hover board, a webmail service, or a ten-year-old PC running Windows Vista, can potentially take a sudden nosedive. Hard drives crash, a lot. Ransomware is as real a threat as your house being robbed, and sometimes technology isn’t even to blame. Natural disasters: Fires, floods, tornados, hurricanes…you name it, they all happen without warning. Laptops get stolen. Point is, you need insurance and assurance that your protected when s**t hits the fan.
Some examples of data protection software and online subscription methods that you may already be using that most believe are providing the same benefits and protection as a managed service provider would:
- EaseUS Todo Backup Free
- Google Backup and Sync
- Cobian Backup
- Paragon Backup and Recovery
- FBackup
- COMODO Backup
- AOMEI Bakcupper Standard
- FileFort Backup
- BackUp MakerDriveImage XML
- Carbonite
- Barracuda
- Mosey Online
Now this isn’t to say that these subscriptions and software’s are not reputable options that can get the job done, but are often done incorrectly or not frequently enough and when the stuff does hit the fan, clients are left crippled and wondering where they possibly went wrong and how in the world they are going to recover without years’ worth of information. This is when the emergency unfolds and the calls and pleas of desperation for CCSI to please figure out a way to find their backed-up information come in.
The facts Are:
- A managed service provider is paid to ensure that your businesses information is backed up, protected and up to date, eliminating that one extra thing for you to do to try and save yourself a few bucks.
- The integrity of your backups is not being tested when you do it yourself through these programs. This is a vital component to backups and is often over looked. If the integrity of our backup is no good then everything from that moment forward is a wash and waste of time because it is unrecoverable.
- Backups are not as easy and click, schedule and rest easy like these programs make them seem. They are a daily operation that needs to be closely monitored. In a 30-day period an average of 8 anomalies for a single business happen. Do you really like those odds being left to a program?
- Technology fails and has limitations. You may be confident in your backups, firewalls, anti-malware, but these are all limited in their function. It is where the technology fails that a trained, educated individual cleans up the mess and puts things back to regular working order ensuring the process will deliver the desired result in the future when it is needed. We’ve become too reliant on technology and the click of a button then have an all-out melt down when the easy clicking fails us. Prevent the issue from even happening and do it correct the first time around.
- Backup plans and disaster recovery solutions are NOT ridiculously expensive. The real cost is not if but when a system fails and all of your business information is lost. That is the cost of your entire business and closing your doors for good. Most don’t recover from such events. $100/month to ensure your business vital information is restorable and protected is a very small price to pay in comparison to the alternative of not having it.
- Disaster Recovery planning is the more expensive option of the two but it is quite literally your entire businesses infrastructure, every single file, customer, business specific application, email…etc. a digital copy of your business readily available to be sent to another server at any location should the need arise. More expensive yes, also smarter…
The advantage of backing up data and preparing for disaster recovery is that the tech will provide a safety net on which the company can fall if the worst does happen. CCSI provides solutions to implement either with affordable rates and plans to keep your business protected, up and running regardless of what the word throws at you.










 Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are wired equivalent Privacy (WEP) and WiFi Protected Access (WPA).
Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are wired equivalent Privacy (WEP) and WiFi Protected Access (WPA). euven. The discovery of the weakness in the wireless security protocol, WPA2, that is used to protect the vast majority of WiFi connections shows how hackers are able to inject PC viruses into internet networks, read peoples passwords, credit card numbers, eavesdrop on private conversations, read emails and view photographs sent over the web. Full disclosure and view of your every click, purchase and move throughout your personal or businesses entire network. Connecting to a secure network requires a four-way “handshake” between a device and a router to ensure that nobody else can decrypt the traffic. Mathy Vanhoef found a way to install a new “key” used to encrypt the communications onto the network, allowing a hacker to gain access to the data.
euven. The discovery of the weakness in the wireless security protocol, WPA2, that is used to protect the vast majority of WiFi connections shows how hackers are able to inject PC viruses into internet networks, read peoples passwords, credit card numbers, eavesdrop on private conversations, read emails and view photographs sent over the web. Full disclosure and view of your every click, purchase and move throughout your personal or businesses entire network. Connecting to a secure network requires a four-way “handshake” between a device and a router to ensure that nobody else can decrypt the traffic. Mathy Vanhoef found a way to install a new “key” used to encrypt the communications onto the network, allowing a hacker to gain access to the data.







