The people you employ should be your company’s biggest asset. Every day your people create more and more valuable data for your business, but when it comes to protecting that data, your current defenses can’t keep up.

With the speed cyber criminals are moving and the pace technology evolves, today’s advanced threats are designed to bypass traditional solutions. Targeting the way your people work to gain access to your sensitive information. This could be phishing attacks that appear as personal emails from colleagues, anti-malware software providing a false sense of security, or any number of new methods which appear every day. With Proofpoint, you can protect the information your people create and stop security threats before they happen.
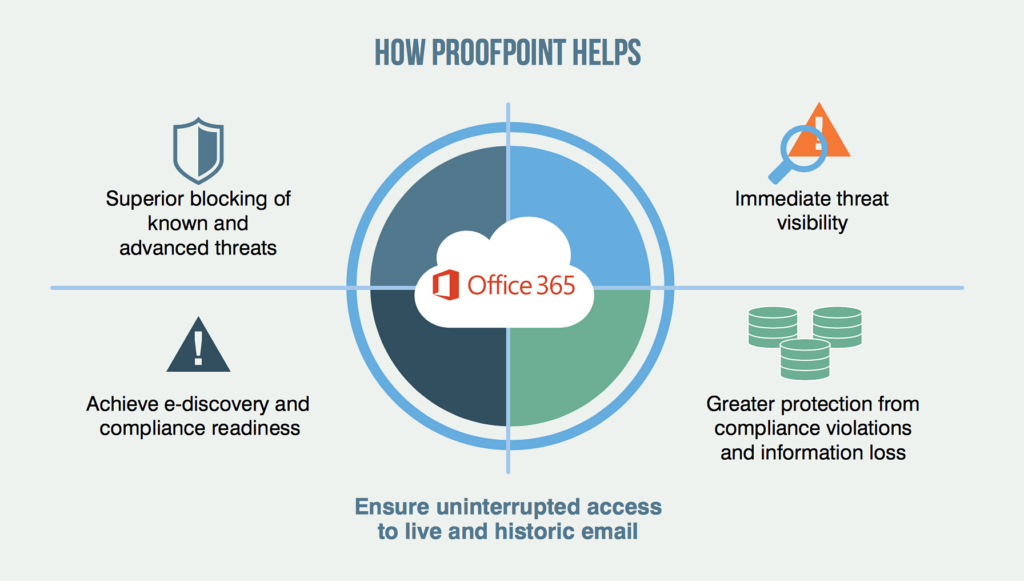
Proofpoint’s solutions combine deep insights across the attack chain with advanced technology to stop attacks anywhere your people work. On network or off, on any device. Enabled by the cloud, within seconds Proofpoint can see everything, correlate across existing defenses and protect everywhere. If an incident is detected Proofpoint allows you to confirm compromises and enable rapid responses reducing the impact of attacks or stop them from happening in the first place.
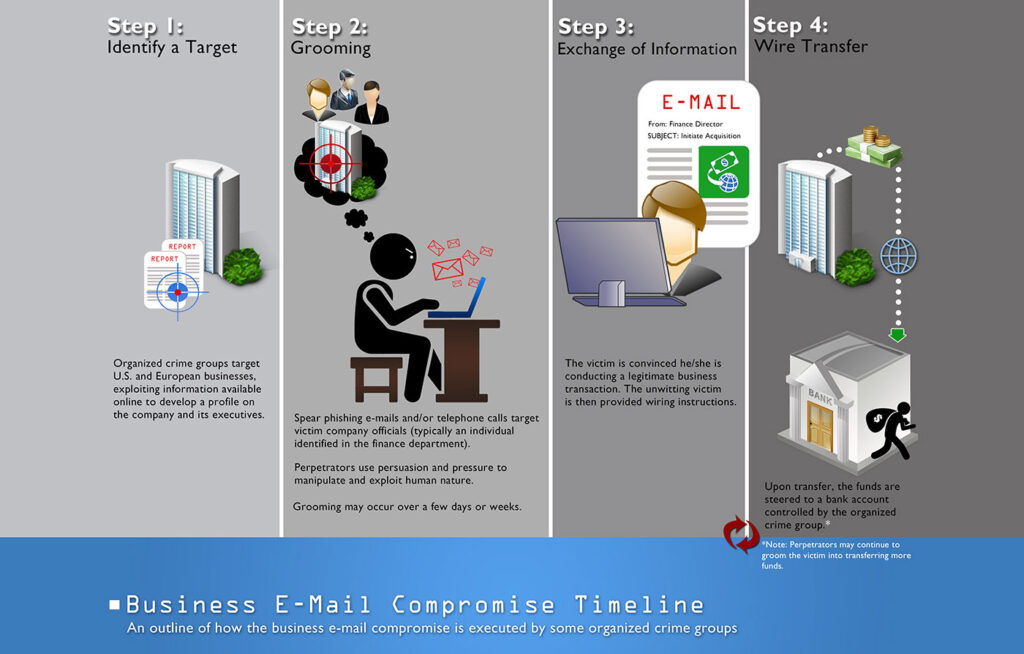
Email fraud, also called Business Email Compromise (BEC) is a type of phishing that preys on your trust. Unlike most email attacks, email fraud doesn’t use malware attachments nor does it use malicious links or other common phishing techniques. Instead it relies on social engineering in order to trick you into doing something the attackers want. According to the FBI email fraud attacks have more than doubled since 2017. Costing an estimated 12 billion dollars since 2013. So how do you detect email fraud?
When you receive an email from a co-worker it feels safe, but that message might not be from them at all. Highly targeted imposter email attacks are the biggest threat facing enterprises today. Costing 3.1 billion dollars in the past two years alone. 95% of those attacks spoof legitimate domains to target your organization. This means cyber criminals create a fake email address using your domain tricking recipients into giving up valuable data, credentials, and funds. It takes just one malicious email to wreak havoc on your organization, but only if it reaches the inbox.
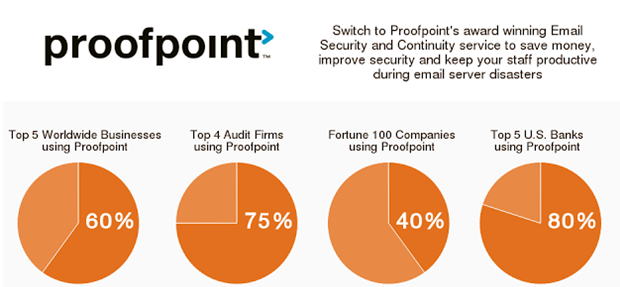
Proofpoint Email Security Filtering can eliminate the devastating impact of imposter email fraud. Leveraging the power of email authentication which enables you to detect block and respond to threats before they reach your employees. With email fraud defense you gain full visibility into your email ecosystem not only will you see who is sending emails on your behalf, but you’ll also get recommendations on how to authorize legitimate senders by authenticating all of the good messages you can start blocking the bad. Combined with other Proofpoint email protection capabilities the multi-layered approach empowers your security team to respond quickly and accurately to even the most sophisticated threats.
Take the first step in protecting your business and contact Customized Computer Services Inc. We work with our clients to develop protocols for best practice and monitor your IT infrastructure to protect against cyber threats.
Customized Computer Services, Inc. is a Managed IT Service Provider, we have been serving the Dallas-Fort Worth Area for 31 years. Contact us to find out how we can help your business stay one step ahead with your IT.

