What is Two Factor Authentication?
Having a password for access into your account or system is the first step into protecting yourself from a hacker attack, but hackers have become very good at getting into systems that use just username and password for access. Usernames and passwords can be easily cracked, captured, and leaked. Today more and more businesses are investing in two factor authentication (2FA). Just what is two factor authentication? Two factor Authentication makes entering into the system more personal. A password is personal but two factor authentication relies on other factors such as: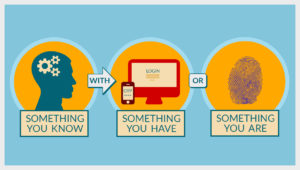
Something you know: your username and password combination or a pin.
Something you have: a bank card, mobile device, smart watch or another device that you have deemed safe.
Something you are: using biometrics such as facial recognition, fingerprints, retinal scans and voice recognition.
By requiring a user to verify their identity with two or more of these unique ways this allows the system to extend security beyond using just a password to access the system. 2FA manages to make this more difficult by adding a second layer of defense. While passwords alone grant access by asking for “something you know,” 2FA requires both this and “something you have” in order to grant access. This means that even if someone has acquired your password, unless they’re you and have your phone or other trusted device in their hand, it will be much more difficult for them to gain access to your accounts.
How does the second factor work?
After you enter your password — the first authentication factor — the second factor usually arrives by SMS. That is, you’ll get a text with a numerical code that you’ll then need to enter to log into your account. Unlike a PIN code for a debit card, a 2FA code is used only one time; each time you log into that account, you’ll be sent a new code.
You can use an authentication app that receives codes instead of having them texted to you for added security. Receiving codes by SMS is less secure than using an authentication app. A hacker can intercept a text message or convincing your cell phone carrier to transfer it to another device. Or if you sync text messages to your computer a hacker can gain access.
Benefits of Two Factor Authentication
Improved Security: Since passwords can be forgotten or lost most people remember them by writing them down somewhere and it can easily fall into the wrong hands. Passwords can be captured by hackers if the PC has been compromised. With 2FA the second line of defense comes into play even if the first factor has failed your data is safe as the hacker won’t have the One Time Password (OTP) necessary to log in.
Reduced Data Theft: Identity theft has become a serious issue in last few years. Through ID theft, a thief can use your name to break into your accounts and can make huge purchases, thereafter leaving a ton of debt for you to pay. 2FA is a very effective way to reduce cyber crimes like identity theft, hacking and phishing.
Increased productivity: With 2FA, more and more companies are allowing their employees to work remotely. Since employees are able to access systems and critical work on the go, the productivity levels increase significantly. 2FA with SSL VPN is one of the most popular security solutions present today.
Reducing operational costs: 2FA also helps companies cut down their operational costs. With this reliable information security solution, the employees can access databases, servers and web portals securely from their devices. All they need to do is to install One Time Password generation software into their phones. This software generates the OTP and is in time sync with the server.
Customized Computer Services Inc., (CCSI) has been recognized as a leader in implementation of cyber security. We have implemented 2FA for many of our clients to protect their business and their clients from cyber threats. Contact us to help protect your business and clients from cyber threats.

