
by Matthew Perdue | Oct 16, 2018 | IT Services |
What is Two Factor Authentication?
Having a password for access into your account or system is the first step into protecting yourself from a hacker attack, but hackers have become very good at getting into systems that use just username and password for access. Usernames and passwords can be easily cracked, captured, and leaked. Today more and more businesses are investing in two factor authentication (2FA). Just what is two factor authentication? Two factor Authentication makes entering into the system more personal. A password is personal but two factor authentication relies on other factors such as: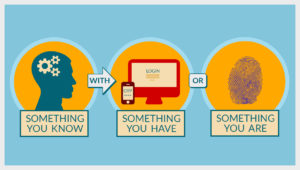
Something you know: your username and password combination or a pin.
Something you have: a bank card, mobile device, smart watch or another device that you have deemed safe.
Something you are: using biometrics such as facial recognition, fingerprints, retinal scans and voice recognition.
By requiring a user to verify their identity with two or more of these unique ways this allows the system to extend security beyond using just a password to access the system. 2FA manages to make this more difficult by adding a second layer of defense. While passwords alone grant access by asking for “something you know,” 2FA requires both this and “something you have” in order to grant access. This means that even if someone has acquired your password, unless they’re you and have your phone or other trusted device in their hand, it will be much more difficult for them to gain access to your accounts.
How does the second factor work?
After you enter your password — the first authentication factor — the second factor usually arrives by SMS. That is, you’ll get a text with a numerical code that you’ll then need to enter to log into your account. Unlike a PIN code for a debit card, a 2FA code is used only one time; each time you log into that account, you’ll be sent a new code.
You can use an authentication app that receives codes instead of having them texted to you for added security. Receiving codes by SMS is less secure than using an authentication app. A hacker can intercept a text message or convincing your cell phone carrier to transfer it to another device. Or if you sync text messages to your computer a hacker can gain access.
Benefits of Two Factor Authentication
Improved Security: Since passwords can be forgotten or lost most people remember them by writing them down somewhere and it can easily fall into the wrong hands. Passwords can be captured by hackers if the PC has been compromised. With 2FA the second line of defense comes into play even if the first factor has failed your data is safe as the hacker won’t have the One Time Password (OTP) necessary to log in.
Reduced Data Theft: Identity theft has become a serious issue in last few years. Through ID theft, a thief can use your name to break into your accounts and can make huge purchases, thereafter leaving a ton of debt for you to pay. 2FA is a very effective way to reduce cyber crimes like identity theft, hacking and phishing.
Increased productivity: With 2FA, more and more companies are allowing their employees to work remotely. Since employees are able to access systems and critical work on the go, the productivity levels increase significantly. 2FA with SSL VPN is one of the most popular security solutions present today.
Reducing operational costs: 2FA also helps companies cut down their operational costs. With this reliable information security solution, the employees can access databases, servers and web portals securely from their devices. All they need to do is to install One Time Password generation software into their phones. This software generates the OTP and is in time sync with the server.
Customized Computer Services Inc., (CCSI) has been recognized as a leader in implementation of cyber security. We have implemented 2FA for many of our clients to protect their business and their clients from cyber threats. Contact us to help protect your business and clients from cyber threats. (more…)

by Matthew Perdue | Sep 14, 2018 | IT Services |
Microsoft’s Exchange Online gives you the power of a hosted enterprise email server as opposed to the traditional, on-site email server which requires capital expenditure and associated maintenance costs. The entire Exchange Online infrastructure runs on Microsoft’s Office 365 Cloud Service, it doesn’t matter whether it’s one mailbox or 10,000 mailboxes. From a cost perspective to a functional perspective migrating to or implementing Exchange Online for businesses makes sense. Some example of how Exchange Online can benefit businesses:
A Professional Image
If you are looking to make an impression on potential clients and customers, a domain based email can give just that a trusted image of a company that is established. Having a company name to the email helps clients to remember and in case contact information is lost it allows them to recall the company name making it easier to get in touch with you.
Business Continuity
Exchange Online uses Microsoft’s global server infrastructure which provides full redundancy, disaster recovery and a continuous uptime guarantee. Exchange online also comes with data loss prevention (DLP) capabilities which prevents users from sending sensitive information to unauthorized people. Exchange offers continuous access to data and offers protection from unauthorized viewing of information. Exchange online is accessible anytime and anywhere you are not restricted by location which allows for business continuity.
Cyber Security and Spam Free
With Cyber Security threats on the rise Exchange Online comes with measures that prevent hackers from getting access and control of your account. They also come with filters that prevent Spam and prevent spam from reaching your clients mail boxes.
Hybrid Flexibility
One of Exchange Online primary selling points for mid-size and enterprise organizations is its hybrid flexibility. Deploying email in a hybrid configuration an organization can keep some user mailboxes on their on-premise Exchange server while moving others to Exchange Online. Exchange Online allows for a seamless staged migration from an on premise sever to the cloud.
Large Mailbox Capacity and Emails
Exchange Online has 50 GB mailboxes; 150 GB archive mailboxes; 150 MB email sizes. Employees will never have to worry about managing their mailbox growth again. Keep everything! Send anything! Every couple of years Microsoft increases the limits. Shared mailboxes and resource mailboxes have a 50 GB limit too, and the best part? Shared mailboxes and resource mailboxes are completely free. Every team can have a shared mailbox (marketing, sales, help desk), and every conference room can be automatically managed through Exchange Online, for free!
Compliance
Exchange Online meets many compliance and regulations certifications. Microsoft uses third-party auditors to certify they meet the compliance and regulatory goals. Not only does Exchange Online meet large regulations such as ISO 27001, European Union (EU) Model Clauses, the Health Insurance Portability and Accountability Act Business Associate Agreement (HIPAA BAA), and the Federal Information Security Management Act (FISMA) but Office 365 is also designed to meet local requirements for data management.
The Benefits of implementing or migrating to Microsoft Exchange Online is long and it simply brings more to the table than the traditional on-site email servers. Contact us at Customized Computer Services, Inc. (CCSI) to give your business the power of a hosted enterprise email server.

by Matthew Perdue | Aug 14, 2018 | IT Services |
What is Synology NAS?
NAS (Network Attached Storage) is a data storage device that connects to your home or office network and allows multiple people to easily store, share, and protect files and other data. By integrating hardware and software, Synology NAS delivers a fine tuned, hassle free performance. Extensive compatibility with hard drives and peripheral devices, such as network cameras, routers, or DLNA devices, allows for easy integration into your environment. Synology NAS is designed with security, redundancy and easy maintenance in mind. Homes and business can take advantage of solutions of all sizes, ranging from single driver server to rackmount models that are expandable over one petabyte.
In the past it was quite an easy decision for an expanding business deploy a windows server, but with the advancement of Network Attached Storage devices the decision is no longer clear cut. These devices now contain very sophisticated operating systems of their own. Not only can you share data but you can install apps. These apps provide you with increased functionality. For example, you can use your Synology device as a DVR base station for your security system. You can also install apps on your mobile devices that will allow you to access your data from anywhere. Synology devices can host VPN connections, websites and much more. With all this functionality and a cost that’s much less expensive than a traditional server.
Synology lets you consolidate multiple services onto a single device
Use the NAS for your video surveillance
Store, organize, and stream your photos, movies, and TV shows
Run your website from the NAS and use database software like MariaDB
Virtualization and lab use test out VMs and run Docker containers then scale up for business
Connect other devices on a VPN running on the NAS
Deploy your own LDAP and single-sign on services via our applications
Synology has security features that protect your business with encryption/HIPAA compliance
VPN support-Connect to or act as the VPN server
Secure protocols –HTTPS, SFTP/FTPS, SSH
Built-in customizable firewall
Set custom ports for all applications
Security Advisor Tool –Audit NAS security
Two-Factor Authentication [one-time code]
Synology NAS devices are becoming more powerful, small businesses are seeing the benefits of utilizing Synology NAS devices. Customized Computer Services, Inc (CCSI) has helped many of our clients implement Synology for their business. For more information on how Synology can benefit your business contact us at (817) 459-4000.
by Matthew Perdue | Jul 13, 2018 | IT Services

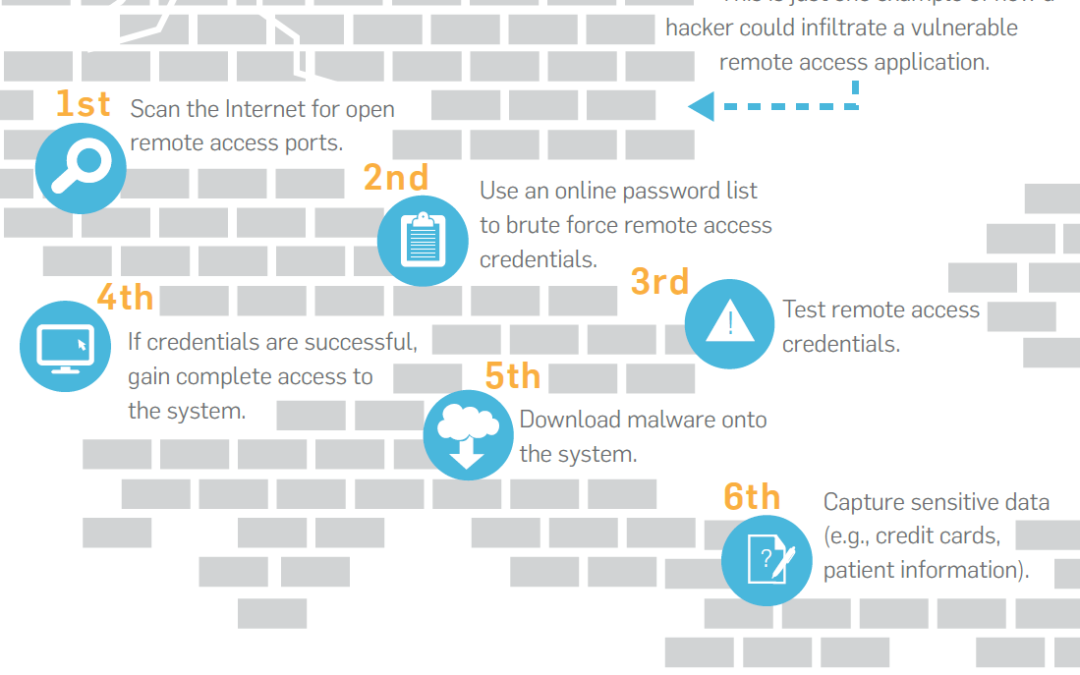
Remote desktop access (RDP) is one of the most common and easiest ways to access computers and servers on your network. For businesses with remote users, this is a common practice, but most are unaware of the security risks this opens them up to. Even those who are aware of the risks often still choose the ease and cost savings that RDP provides. So, what is RDP and what makes it such a security risk? Simply put, RDP is a tool to remotely connect and control a PC or server on a network. By default, RDP uses the port 3389. Leaving this port open means that attackers can find and then launch a ‘brute force’ attack. Sending 1000s of random usernames and passwords at the server until they are in. Once they are on the system there is no end to the damage they can cause. From viruses to Ransomware, costing tens of thousands of dollars in damage if not more. Even if attackers do not make their way in, you and your business can still feel the impact. These brute force attacks hit your server with thousands of failed login attempts which can slow performance and productivity to a crawl. While there are some workarounds to better secure yourself against these kinds of attacks; changing port numbers or using third party software to detect and mitigate the effects of brute force attacks. We at CCSI believe the best option is to remove the problem all together.
CCSI has been migrating it’s clients to the more secure and more reliable use of VPN’s. VPN (or Virtual Private Network) creates an encrypted ‘tunnel’ into the network making it so that RDP ports will no longer need to be opened on the firewall. No open ports means there is nothing for attackers to attempt to force their way in to.








