
by Matthew Perdue | Nov 14, 2018 | IT Services |
The Internet of Things (IoT) continues to bring people, processes, data and things together in a variety of environments. From enterprise spaces to entertainment venues, the IoT is expanding to include a host of intelligent devices such as LED lighting, security cameras, and WiFi access points.
As more of our devices are become intelligent devices, Contractors and IT professionals are turning over to Power over Ethernet cabling (PoE). As means of powering and also controlling the multitude of intelligent devices connected to their network.
What is Power-over-Ethernet?
Power-over-Ethernet is a means of carrying power and data to a device using copper communications cabling. The main advantage of Power over Ethernet (PoE) is delivery of data AND power over one Cat5e/Cat6 Ethernet cable. PoE ends the need for AC/DC power supplies and outlets. A remote installation costs less than fiber as no electrician is required. Ethernet cable costs less and is often already installed in buildings. A 2013 study conducted by the IEEE found that Power-over-Ethernet was twice as efficient at distributing power as traditional electrical cabling, reducing the power lost in the channel by at least half.1
When should PoE be used?
Power-over-Ethernet is used to power and control many types of intelligent devices including LED lighting, HVAC and climate control systems, IP security cameras and access controls, IP televisions and displays, and WiFi access points. PoE allows you to add a device in awkward or remote locations. PoE is not recommended for sending network data over long distances, or for extreme temperatures unless industrial designation is present.
For building managers, IT professionals and contractors tasked with installing and managing possibly hundreds of intelligent devices, PoE offers a simple solution. Not only does it provide more efficient power and data throughput to the device compared to traditional cable setups, and a potential for cost savings as a result, but it also allows for a variety of digital devices placed throughout an environment to be powered and controlled utilizing a single communications network.
The increase popularity of PoE
With the continuous development and growth of the Internet of Things and the increase in interconnected, data driven devices within an enterprise, PoE cabling has become very popular. In 2014 alone, PoE saw an uptake of 80% in VoIP applications. In the same year, a reported 30% of CCTVs, 20% of access controls and Wi-Fi access points, and 10% of lighting were powered by PoE.2
Types of Speed Offered by PoE
PoE costs less than fiber and is delivering higher and higher data speeds.
Thanks to widespread adoption of IEEE 802.3bz technology, manufacturers are spending more on product development. Data delivery rates are now at 1 Gbps (10/100/1000 Mbps) over Cat5e and Cat6. The new IEEE 802.3bz standard has the capacity to deliver speeds of 2.5 to 5 Gbps over 100m with an immediate view toward 10 Gbps.
High-definition streaming only requires 400 Mbps. A network could easily stream a training video while others work and check email.
PoE has more than enough data speed to support devices in a small LAN.
Power over Ethernet power delivery
New IEE 802.3 versions for PoE have been published over time address market demands for higher power levels to be delivered to powered devices. The following shows the power delivered to the powered device (PD) for each revision:
• IEEE 802.3af–2003 up to 12.95 W
• IEEE 802.3at–2009 up to 25.5 W (2–pairs, medium power) – a.k.a. Poe+
• IEEE 802.3at–2009 up to 51 W (4–pairs, high power) – a.k.a. Poe+
• IEEE 802.3bt–draft 2.0 up to 71 W (a.k.a PoE++, 4PPoE)
With the growth of Internet of Things (IoT) and the continued development of interconnected, data driven devices the implementation of PoE cabling seem endless. Contact Customized Computer Services, Inc. to find out we can help your company improve its efficiency by using Power-over-Ethernet cabling to connect to the Internet-of-Things.
1. BSRIA (2015). Convergence and Big Data: The Impact on Structured Cabling
2. BSRIA (2015). Convergence and Big Data: The Impact on Structured Cabling

by Matthew Perdue | Oct 16, 2018 | IT Services |
What is Two Factor Authentication?
Having a password for access into your account or system is the first step into protecting yourself from a hacker attack, but hackers have become very good at getting into systems that use just username and password for access. Usernames and passwords can be easily cracked, captured, and leaked. Today more and more businesses are investing in two factor authentication (2FA). Just what is two factor authentication? Two factor Authentication makes entering into the system more personal. A password is personal but two factor authentication relies on other factors such as: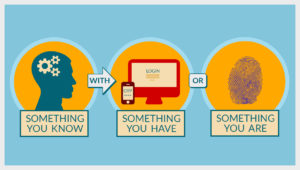
Something you know: your username and password combination or a pin.
Something you have: a bank card, mobile device, smart watch or another device that you have deemed safe.
Something you are: using biometrics such as facial recognition, fingerprints, retinal scans and voice recognition.
By requiring a user to verify their identity with two or more of these unique ways this allows the system to extend security beyond using just a password to access the system. 2FA manages to make this more difficult by adding a second layer of defense. While passwords alone grant access by asking for “something you know,” 2FA requires both this and “something you have” in order to grant access. This means that even if someone has acquired your password, unless they’re you and have your phone or other trusted device in their hand, it will be much more difficult for them to gain access to your accounts.
How does the second factor work?
After you enter your password — the first authentication factor — the second factor usually arrives by SMS. That is, you’ll get a text with a numerical code that you’ll then need to enter to log into your account. Unlike a PIN code for a debit card, a 2FA code is used only one time; each time you log into that account, you’ll be sent a new code.
You can use an authentication app that receives codes instead of having them texted to you for added security. Receiving codes by SMS is less secure than using an authentication app. A hacker can intercept a text message or convincing your cell phone carrier to transfer it to another device. Or if you sync text messages to your computer a hacker can gain access.
Benefits of Two Factor Authentication
Improved Security: Since passwords can be forgotten or lost most people remember them by writing them down somewhere and it can easily fall into the wrong hands. Passwords can be captured by hackers if the PC has been compromised. With 2FA the second line of defense comes into play even if the first factor has failed your data is safe as the hacker won’t have the One Time Password (OTP) necessary to log in.
Reduced Data Theft: Identity theft has become a serious issue in last few years. Through ID theft, a thief can use your name to break into your accounts and can make huge purchases, thereafter leaving a ton of debt for you to pay. 2FA is a very effective way to reduce cyber crimes like identity theft, hacking and phishing.
Increased productivity: With 2FA, more and more companies are allowing their employees to work remotely. Since employees are able to access systems and critical work on the go, the productivity levels increase significantly. 2FA with SSL VPN is one of the most popular security solutions present today.
Reducing operational costs: 2FA also helps companies cut down their operational costs. With this reliable information security solution, the employees can access databases, servers and web portals securely from their devices. All they need to do is to install One Time Password generation software into their phones. This software generates the OTP and is in time sync with the server.
Customized Computer Services Inc., (CCSI) has been recognized as a leader in implementation of cyber security. We have implemented 2FA for many of our clients to protect their business and their clients from cyber threats. Contact us to help protect your business and clients from cyber threats. (more…)

by Matthew Perdue | Sep 14, 2018 | IT Services |
Microsoft’s Exchange Online gives you the power of a hosted enterprise email server as opposed to the traditional, on-site email server which requires capital expenditure and associated maintenance costs. The entire Exchange Online infrastructure runs on Microsoft’s Office 365 Cloud Service, it doesn’t matter whether it’s one mailbox or 10,000 mailboxes. From a cost perspective to a functional perspective migrating to or implementing Exchange Online for businesses makes sense. Some example of how Exchange Online can benefit businesses:
A Professional Image
If you are looking to make an impression on potential clients and customers, a domain based email can give just that a trusted image of a company that is established. Having a company name to the email helps clients to remember and in case contact information is lost it allows them to recall the company name making it easier to get in touch with you.
Business Continuity
Exchange Online uses Microsoft’s global server infrastructure which provides full redundancy, disaster recovery and a continuous uptime guarantee. Exchange online also comes with data loss prevention (DLP) capabilities which prevents users from sending sensitive information to unauthorized people. Exchange offers continuous access to data and offers protection from unauthorized viewing of information. Exchange online is accessible anytime and anywhere you are not restricted by location which allows for business continuity.
Cyber Security and Spam Free
With Cyber Security threats on the rise Exchange Online comes with measures that prevent hackers from getting access and control of your account. They also come with filters that prevent Spam and prevent spam from reaching your clients mail boxes.
Hybrid Flexibility
One of Exchange Online primary selling points for mid-size and enterprise organizations is its hybrid flexibility. Deploying email in a hybrid configuration an organization can keep some user mailboxes on their on-premise Exchange server while moving others to Exchange Online. Exchange Online allows for a seamless staged migration from an on premise sever to the cloud.
Large Mailbox Capacity and Emails
Exchange Online has 50 GB mailboxes; 150 GB archive mailboxes; 150 MB email sizes. Employees will never have to worry about managing their mailbox growth again. Keep everything! Send anything! Every couple of years Microsoft increases the limits. Shared mailboxes and resource mailboxes have a 50 GB limit too, and the best part? Shared mailboxes and resource mailboxes are completely free. Every team can have a shared mailbox (marketing, sales, help desk), and every conference room can be automatically managed through Exchange Online, for free!
Compliance
Exchange Online meets many compliance and regulations certifications. Microsoft uses third-party auditors to certify they meet the compliance and regulatory goals. Not only does Exchange Online meet large regulations such as ISO 27001, European Union (EU) Model Clauses, the Health Insurance Portability and Accountability Act Business Associate Agreement (HIPAA BAA), and the Federal Information Security Management Act (FISMA) but Office 365 is also designed to meet local requirements for data management.
The Benefits of implementing or migrating to Microsoft Exchange Online is long and it simply brings more to the table than the traditional on-site email servers. Contact us at Customized Computer Services, Inc. (CCSI) to give your business the power of a hosted enterprise email server.

by Matthew Perdue | Aug 14, 2018 | IT Services |
What is Synology NAS?
NAS (Network Attached Storage) is a data storage device that connects to your home or office network and allows multiple people to easily store, share, and protect files and other data. By integrating hardware and software, Synology NAS delivers a fine tuned, hassle free performance. Extensive compatibility with hard drives and peripheral devices, such as network cameras, routers, or DLNA devices, allows for easy integration into your environment. Synology NAS is designed with security, redundancy and easy maintenance in mind. Homes and business can take advantage of solutions of all sizes, ranging from single driver server to rackmount models that are expandable over one petabyte.
In the past it was quite an easy decision for an expanding business deploy a windows server, but with the advancement of Network Attached Storage devices the decision is no longer clear cut. These devices now contain very sophisticated operating systems of their own. Not only can you share data but you can install apps. These apps provide you with increased functionality. For example, you can use your Synology device as a DVR base station for your security system. You can also install apps on your mobile devices that will allow you to access your data from anywhere. Synology devices can host VPN connections, websites and much more. With all this functionality and a cost that’s much less expensive than a traditional server.
Synology lets you consolidate multiple services onto a single device
Use the NAS for your video surveillance
Store, organize, and stream your photos, movies, and TV shows
Run your website from the NAS and use database software like MariaDB
Virtualization and lab use test out VMs and run Docker containers then scale up for business
Connect other devices on a VPN running on the NAS
Deploy your own LDAP and single-sign on services via our applications
Synology has security features that protect your business with encryption/HIPAA compliance
VPN support-Connect to or act as the VPN server
Secure protocols –HTTPS, SFTP/FTPS, SSH
Built-in customizable firewall
Set custom ports for all applications
Security Advisor Tool –Audit NAS security
Two-Factor Authentication [one-time code]
Synology NAS devices are becoming more powerful, small businesses are seeing the benefits of utilizing Synology NAS devices. Customized Computer Services, Inc (CCSI) has helped many of our clients implement Synology for their business. For more information on how Synology can benefit your business contact us at (817) 459-4000.
by Matthew Perdue | Jul 13, 2018 | IT Services

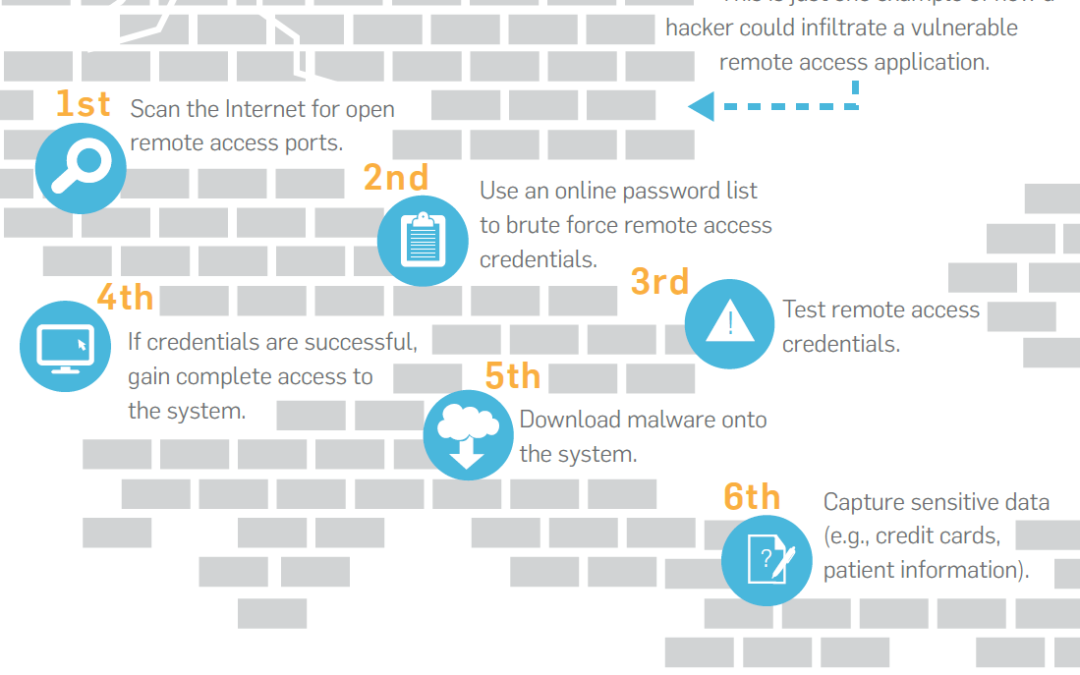
Remote desktop access (RDP) is one of the most common and easiest ways to access computers and servers on your network. For businesses with remote users, this is a common practice, but most are unaware of the security risks this opens them up to. Even those who are aware of the risks often still choose the ease and cost savings that RDP provides. So, what is RDP and what makes it such a security risk? Simply put, RDP is a tool to remotely connect and control a PC or server on a network. By default, RDP uses the port 3389. Leaving this port open means that attackers can find and then launch a ‘brute force’ attack. Sending 1000s of random usernames and passwords at the server until they are in. Once they are on the system there is no end to the damage they can cause. From viruses to Ransomware, costing tens of thousands of dollars in damage if not more. Even if attackers do not make their way in, you and your business can still feel the impact. These brute force attacks hit your server with thousands of failed login attempts which can slow performance and productivity to a crawl. While there are some workarounds to better secure yourself against these kinds of attacks; changing port numbers or using third party software to detect and mitigate the effects of brute force attacks. We at CCSI believe the best option is to remove the problem all together.
CCSI has been migrating it’s clients to the more secure and more reliable use of VPN’s. VPN (or Virtual Private Network) creates an encrypted ‘tunnel’ into the network making it so that RDP ports will no longer need to be opened on the firewall. No open ports means there is nothing for attackers to attempt to force their way in to.

by Mellissa Lologo | May 25, 2018 | IT Services |

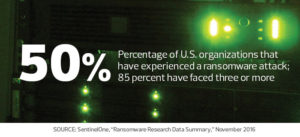
Recent ransomware attacks like Wanna and Petya have spread largely unchecked through corporate networks in recent months, extorting money to restore your data and regain control of your computers. CCSI has informed our customers in the past and some have experienced the pain of Ransomware. These attacks have not stopped and the measures CCSI has taken to detect and stop these types of attacks have been successful in reducing the consequences when such an attack occurs. For a better understanding of what it is your up against, let’s break down how the hackers are infiltrating your systems, to begin with, and some recommendations to beef up the security by utilizing technologies you already have or steering you in the right direction of what to get.
HOW HACKERS PIN-POINT AND LAUNCH RANSOMWARE
Finding and exploiting a business is not determined by the size or success of a business, hackers don’t use their crazy good tech skills to research businesses annual revenue as a measure to determine that your business will be a good one to hack because it makes lots of money. Although, very successful fortune 500 companies have fallen victim to ransomware attacks it was not because of their success no, no. Hole in the wall pizzeria’s, mom and pop trophy shops, start up’s, all the way to government agencies, multi-national corporations and county hospitals have all been targeted not because of their net worth but because of weak points in your network’s security/firewall are what these guys look for but simply because they could “walk” right in.
So, how do they find these weak points? Although there’s a myriad of ways hackers make their way into and infect a network the most common are:
Remote Access to Servers and Workstations:
Even though remote access to your servers and workstations, to work from home or elsewhere, is a must, we highly recommend closing remote desktop access directly from the internet. As hackers have been able to crack passwords and log into networks, they then manually run the ransomware executables directly on servers and in some cases workstations CCSI is recommending that anyone who needs remote access to servers or desktops be required to use a VPN client to connect to their office network, then they can establish a remote desktop connection to servers or desktops in a safe and secure environment. This will add an extra step to make these connections but the security this gives is well worth the extra step.
Aging Firewalls:
Everyone knows we need firewalls but, as any good network admin will tell you, owning a firewall isn’t the same as getting the most out of your firewall. Your security posture has to adapt continuously to deal with the ever-shifting threat landscape and the emergence of new threats like advanced, worm-like ransomware. Modern firewalls are purpose-built to defend against these kinds of attacks, but they need to be given an opportunity to do their job. There are multiple methods of entry from a hackers standpoint these few currently being the most used:
- The “Over-Seas I.P.” Method: An American based company with multiple locations across the U.S. but has hosted backup services that originate in Russia. We are able to tell that an IP address is originating from Russia due to the placement of the octets (the first 3 numbers) in the I.P. addr
 ess, no different than an area code. Firewalls are intelligent enough (with the correct upgrades/abilities) to constantly compare and identify where an IP address is coming from and the option to exclude or accept IP ranges for certain locations. So in this instance, we would set a rule that I.P. addresses trying to gain access can be from the certain geo-locations of where the business is located in the U.S> and the specific geo-location of the hosted backup services in Russia. All other I.P.’s are excluded. In order to avoid the overseas hackers being granted ANY type of access to the network, you need this feature enabled assuming your existing firewalls has the feature/capability.
ess, no different than an area code. Firewalls are intelligent enough (with the correct upgrades/abilities) to constantly compare and identify where an IP address is coming from and the option to exclude or accept IP ranges for certain locations. So in this instance, we would set a rule that I.P. addresses trying to gain access can be from the certain geo-locations of where the business is located in the U.S> and the specific geo-location of the hosted backup services in Russia. All other I.P.’s are excluded. In order to avoid the overseas hackers being granted ANY type of access to the network, you need this feature enabled assuming your existing firewalls has the feature/capability.
- Common File Malware: While Wanna and Petya spread like worms, many ransomware variants leverage social engineering tricks through phishing email attacks, spam, or web downloads to gain entry to your network through more conventional means. These attacks often start as cleverl
 y crafted malware lurking in common files like Microsoft Office documents, PDFs, or executables such as updates for common trusted applications. Hackers have become very effective at making these files seem benign or obfuscating the malware to get past traditional signature-based antivirus detection. As a result of this new breed of file-based malware, sandboxing technology has become an essential security layer at your network perimeter. Fortunately, cloud-based sandboxing typically doesn’t require any additional hardware or software deployment – it simply identifies suspect files at the gateway and sends them to a safe sandboxing infrastructure in the cloud to detonate active content and monitor the behavior over time. It can be extremely effective at blocking unknown threats like new ransomware attacks before they enter the network.
y crafted malware lurking in common files like Microsoft Office documents, PDFs, or executables such as updates for common trusted applications. Hackers have become very effective at making these files seem benign or obfuscating the malware to get past traditional signature-based antivirus detection. As a result of this new breed of file-based malware, sandboxing technology has become an essential security layer at your network perimeter. Fortunately, cloud-based sandboxing typically doesn’t require any additional hardware or software deployment – it simply identifies suspect files at the gateway and sends them to a safe sandboxing infrastructure in the cloud to detonate active content and monitor the behavior over time. It can be extremely effective at blocking unknown threats like new ransomware attacks before they enter the network.

Best Practices for Firewall and Network Configuration:
It’s important to keep in mind that IPS, sandboxing and all other protection the firewall provides is only effective against traffic that is actually traversing the firewall and where suitable enforcement and protection policies are being applied to the firewall rules governing that traffic. So with that in mind, follow these best practices for preventing the spread of worm-like attacks on your network.
- Ensure you have the right protection: Including a modern high-performance nextgen firewall IPS engine and sandboxing solution.
- Reduce the surface area of attack; as much as possible by thoroughly reviewing and revisiting all port-forwarding rules to eliminate any non-essential open ports. Every open port represents a potential opening in your network. Where possible, use VPN to access resources on the internal network from outside rather than port-forwarding.
- Be sure to properly secure any open ports; by applying suitable IPS protection to the rules governing that traffic
- Apply sandboxing to web and email traffic; to ensure all suspicious active files coming in through web downloads and as email attachments are being suitably analyzed for malicious behavior before they get onto your network.
- Minimize the risk of lateral movement; within the network by segmenting LANs into smaller, isolated zones or VLANs that are secured and connected together by the firewall. Be sure to apply suitable IPS policies to rules governing the traffic traversing these LAN segments to prevent exploits, worms, and bots from spreading between LAN segments.
- Automatically isolate infected systems: When an infection hits, it’s important that your IT security solution be able to quickly identify compromised systems and automatically isolate them until they can be cleaned up (either automatically or through manual intervention)
Importance of Firewall Performance:
Ransomware, botnets, and other advanced attacks will often work their way through your entire IT infrastructure. A firewall that includes all the technology needed to help protect your organization from the latest attacks is well worth the investment considering the level of protection and security it provides. Upgrading to newer technology is expensive, the reason being mostly the amount of processing required to constantly compare lists of accepted and blocked I.P.’s while performing its other huge task list. This doesn’t mean that you need to rip out or replace your existing firewall and purchase the top of the line one right now. A lot of firewalls come with features capable of the requirements needed to take the proper security steps for protection but just aren’t utilized. If the feature isn’t actively available check to see if there’s an upgrade or patch. If these still don’t cover the needs, contact your CCSI account manager for a full rundown of your existing firewalls capabilities or options to implementing a firewall with the protection your business needs at a price you can afford.













 ess, no different than an area code. Firewalls are intelligent enough (with the correct upgrades/abilities) to constantly compare and identify where an IP address is coming from and the option to exclude or accept IP ranges for certain locations. So in this instance, we would set a rule that I.P. addresses trying to gain access can be from the certain geo-locations of where the business is located in the U.S> and the specific geo-location of the hosted backup services in Russia. All other I.P.’s are excluded. In order to avoid the overseas hackers being granted ANY type of access to the network, you need this feature enabled assuming your existing firewalls has the feature/capability.
ess, no different than an area code. Firewalls are intelligent enough (with the correct upgrades/abilities) to constantly compare and identify where an IP address is coming from and the option to exclude or accept IP ranges for certain locations. So in this instance, we would set a rule that I.P. addresses trying to gain access can be from the certain geo-locations of where the business is located in the U.S> and the specific geo-location of the hosted backup services in Russia. All other I.P.’s are excluded. In order to avoid the overseas hackers being granted ANY type of access to the network, you need this feature enabled assuming your existing firewalls has the feature/capability. y crafted malware lurking in common files like Microsoft Office documents, PDFs, or executables such as updates for common trusted applications. Hackers have become very effective at making these files seem benign or obfuscating the malware to get past traditional signature-based antivirus detection. As a result of this new breed of file-based malware,
y crafted malware lurking in common files like Microsoft Office documents, PDFs, or executables such as updates for common trusted applications. Hackers have become very effective at making these files seem benign or obfuscating the malware to get past traditional signature-based antivirus detection. As a result of this new breed of file-based malware,