3CX – A Modern Phone System Solution
To Learn More Contact Us At
817-459-4000
817-459-4000

If you’ve been a regular reader of our blog then you are probably familiar with all of the ways you should be protecting your business. Whether that is securing your data with regular onsite and offsite backups, protecting your hardware with an always up to date Antivirus and Antimalware application, and protecting your email with intelligent and robust Antispam.
However, you may not be aware that your most valuable asset in the fight against hackers, and your first line of defense, is your users. Every suspicious link, every rogue email that slips through your spam filters is the opening salvo that could lead to costly downtime for your business. All it takes is one careless click for disaster to strike.
So how can you make sure your users are prepared to defend themselves from online attackers?
Breach Secure Now is a comprehensive suite of monitoring, training, and education tools designed to safely and easily get your users up to date on the best practices when it comes to online safety.

AutoPhish: Unlimited, automated campaigns
With mock phishing emails, you can send routine simulated phishing emails, proven to minimize the risk of end-users falling victim to a malicious phishing attempt. Routine phishing instills into your users the very behaviors of IT professionals before they click on any link so that even on the most chaotic of days, they’re ready.

Continuous Education: Weekly micro-training video, quiz & monthly security newsletter
Customized weekly 2-minute ‘micro-training’ videos & short quizzes combined with a monthly security newsletter keep cybersecurity short, engaging, and interactive. With white-labeled emails sent on your behalf to all your users for hands-off management.
Interactive Leaderboard: Friendly competition
Keep track of users’ progress with real time scoring. An interactive leaderboard ignites friendly competition with just their screen name’s honor at stake. For managers, employee names are featured, with a report for performance evaluations, letting you track exactly who needs more time training.

Dark Web Monitoring: Continuous monitoring
Proactively monitor the dark web for compromised account data. The sooner end-users are notified of a breach, the sooner they can change their passwords. End-users also have the ability to scan the dark web for their personal accounts so they can prevent cross contamination between their personal devices and your business network.
For more information, contact Customized Computer Services Inc. We work with our clients to develop protocols for best practice and monitor your IT infrastructure to ensure the security of your accounts.
Customized Computer Services, Inc. is a Managed IT Service Provider, we have been serving the Dallas-Fort Worth Area for 31 years. Contact us to find out how we can help your business stay one step ahead with your IT.

The largest ransomware attack of 2021 has come, and the effects are still being felt.
Over the July 4th weekend, hundreds of businesses and thousands of computers were hit by the REvil Ransomware. This is pretty big news and the attack is still ongoing. At the center of the drama is a company called Kaseya.
Kaseya provides IT management software to businesses who need to monitor and maintain all of their computers. Their ‘Kaseya VSA’ software was hit with a supply chain attack, allowing cyber criminals to inject malicious code into a software update. These software updates was then pushed out to all of the connected devices.
Kaseya VSA is a remote monitoring tool which allows full access to the computers it’s installed on which is useful for IT technicians to diagnose and fix problems remotely, or in this case, deploy software updates. If an MSP which uses this software gets infected then all of their clients are vulnerable to attack.

While Kaseya themselves are only reporting 40 of their customers have been infected, the true number of infected computers is thought to be in the thousands. This is due to the large number of MSPs, or Managed Service Providers who use the VSA software to remotely manage their client’s computers.
We don’t know specifically which companies have been infected, as most infected companied are going to want to stay quiet about the intrusions, though we do know that a chain of supermarkets has been forced to close after their check out systems was ransomed. This chain was a client of one of the MSPs that was attacked.

With CCSI’s Qualified IT Professionals we can help assess your business infrastructure and design tailormade solution to protect you from disasters like these. Whether implementing proper backup planning and disaster recovery, or minimizing the risks of ransomware, we can work with you to implement changes so that your business will be ready to handle it with minimal impact to your daily operations.
For more information, contact Customized Computer Services Inc. We work with our clients to develop protocols for best practice and monitor your IT infrastructure to ensure the security of your accounts.
Customized Computer Services, Inc. is a Managed IT Service Provider, we have been serving the Dallas-Fort Worth Area for 31 years. Contact us to find out how we can help your business stay one step ahead with your IT.

It is common knowledge these days that securing and protecting your data is one of the most important things when it comes to running a business. We’ve already discussed the benefits of proper Backup and Disaster Recovery Planning. With Ransomware attacks at an all-time high and natural disasters costing business owners billions of dollars there is no better time to make sure your business is prepared to react and reduce the impact of these threats.

What is Business Continuity?
Business continuity is not only about having a clear plan of action so your company can function with minimal disruption, but about being able to identify all aspects of your business, how they work together, and where improvements can be made to ensure smooth operation under unforeseen circumstances.

ASSESSMENT
The first step to successful planning is a thorough understanding of the critical functions of your business and identifying weaknesses in your current infrastructure.
DESIGN
Next you will identify solutions to achieve continuity during disruptions. This includes your backup and disaster recovery and the details of the priorities, procedures, responsibilities and resources required to manage an incident and return to operation.

IMPLEMENTATION
Finally, the process of putting the solutions in place. Ensuring all of the protections are ready for when they are needed and that those systems are monitored and maintained.

VALIDATION
This step is an ongoing test of your continuity plan. Carried out in a controlled environment you can test recovery of your business operations without the worry of loss of time or money. Reoccurring on a regular basis, you can ensure your business will be ready if and when an emergency occurs.
With CCSI’s Qualified IT Professionals we can help assess the key components of your business and design a clear plan of action to minimize downtime. We can work with you to implement these changes company wide and validate the effectiveness in a controlled environment, so that when disaster truly does strike, your business will be ready to handle it with minimal impact to your daily operations.
For more information on Business Continuity and Disaster Recovery, contact Customized Computer Services Inc. We work with our clients to develop protocols for best practice and monitor your IT infrastructure to ensure the security of your accounts.
Customized Computer Services, Inc. is a Managed IT Service Provider, we have been serving the Dallas-Fort Worth Area for 31 years. Contact us to find out how we can help your business stay one step ahead with your IT.

Passwords are everywhere. We use them to access our money, our communications, even our social lives.
At first, we used one password for everything, but that wasn’t good enough so we started making our passwords even more complicated and relied on password managers or handwritten notes to organize the dozens or hundreds of unique passwords we use.
But no matter how complex our password system was it was never enough to prevent account takeover, because all it took was one phishing email or database exploit and your password was out in the world.
We’ve talked before about the importance of password security and how even the most complex passwords are not enough to prevent breeches(1) and malicious(2) attacks(3).
Security experts and even the United States Government(4) have expressed the need for increased security and protection in our increasingly online lives and business.
Still, every year the statistics tell the same story or worse;
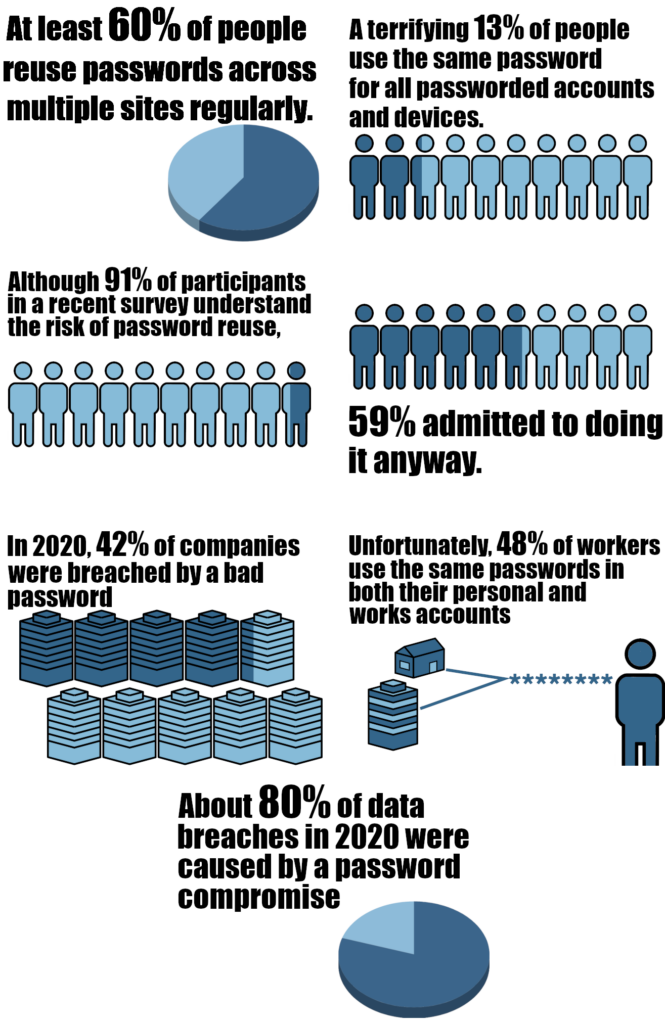
It’s plain to see that relying on passwords alone is not enough to protect yourself or your business.
Two-factor authentication for Office 365 and Hosted Exchange
Two-factor authentication(5) is an extra layer of security designed to ensure that you’re the only person who can access your account, even if someone knows your password.
With two-factor authentication, only you can access your account on a trusted device or the web. When you want to sign in to a new device for the first time, you’ll need to provide two pieces of information—your password and the six-digit verification code that’s automatically displayed on your trusted devices or sent to your phone number.
Because your password alone is no longer enough to access your account, two-factor authentication dramatically improves the security of your account and all the personal information you store with Office 365.
Once signed in, you won’t be asked for a verification code on that device again unless you sign out completely or need to change your password for security reasons. When you sign in on the web, you can choose to trust your browser, so you won’t be asked for a verification code the next time you sign in from that computer.
For more information on how to secure your Office 365 account, contact Customized Computer Services Inc.(6) We work with our clients to develop protocols for best practice and monitor your IT infrastructure to ensure the security of your accounts.
Customized Computer Services, Inc. is a Managed IT Service Provider(7), we have been serving the Dallas-Fort Worth Area for 31 years. Contact us (8) to find out how we can help your business stay one step ahead with your IT.

When running a business, you know the security and ease of having dedicated file servers and a managed user database cannot be overstated, but if you are a small to medium sized company or have multiple locations, it can be hard to justify spending thousands on dedicated servers.

With Synology Network Attached Storage (NAS) you can have that convenience without the cost.
The Synology DiskStation line of NAS provides expandability and customization that allows for added functionality beyond data storage, tailored to your specific needs.
These days, business data is scattered across multiple platforms and devices, from servers to virtual machines, personal computers and cloud applications like Google Drive, Drop Box, or Microsoft One Drive.
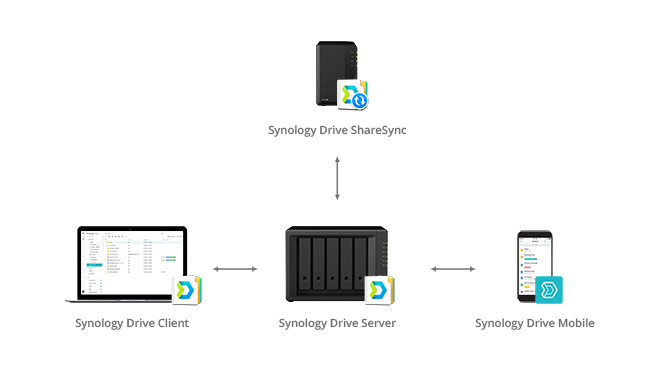
With a Synology NAS all of your important data can be stored in one centralized location allowing your employees access, even when away from the office.
For businesses with multiple locations, you can even set up file replication between Synology devices. No longer will your satellite offices be hampered by slow internet speeds as they try to access files from the primary location.
With Synology Hyper Backup you have the peace of mind of backing up your data to one centralized location. Partner that with Cloud Sync and you can increase the safety of your data with a redundant offsite backup. So even if the worst were to happen, you can rest easy knowing your data can be quickly and easily recovered.
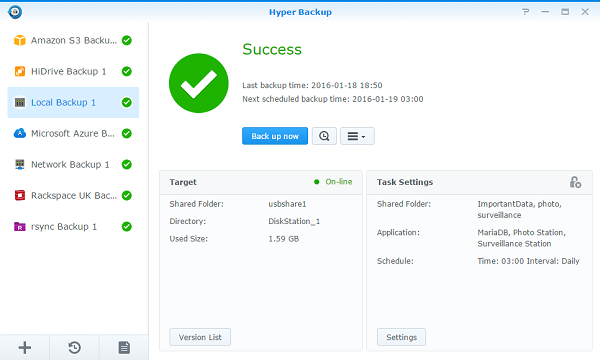
As businesses migrate more and more to cloud based products and online focused collaboration tools many are finding it hard to keep up with the important data shared on these services. Email from Exchange Online, Microsoft Teams messages and attached files, OneNote notebooks, SharePoint libraries, and OneDrive.
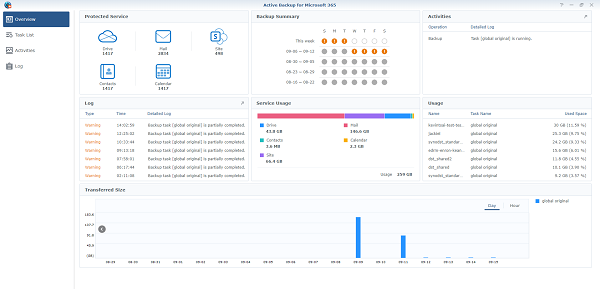
No more will you have to worry about that email from 3 years ago that you may have deleted. Or the document that was shared through MS Teams and now is lost in months and months of message logs.
All of these data sources can be securely backed up with Synology Active Backup for Microsoft 365.
While commonplace in larger businesses, a dedicated active directory server is often out of reach for those with fewer employees. However, the benefits of managing your user accounts through AD are immeasurable, regardless of your business size.
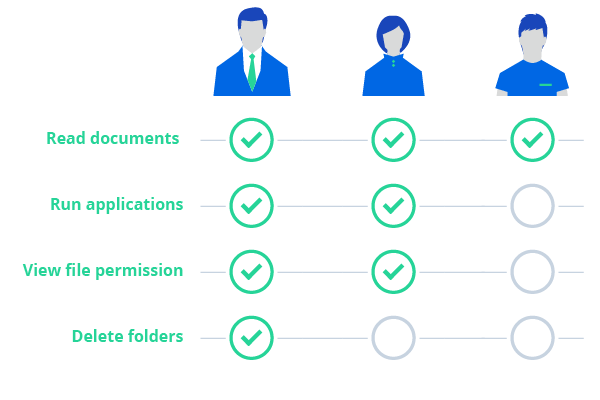
With Synology Active Directory you can create and manage user accounts for all of your employees. Set password rules and expirations to prevent malicious attacks. Set group rules for file access on your network shares and more.
With Synology all of your data, no matter the source, is quickly and easily available to you.
For more information on how to protect your data, contact Customized Computer Services Inc. We work with our clients to develop protocols for best practice and monitor your IT infrastructure to ensure the integrity of your data.
Customized Computer Services, Inc. is a Managed IT Service Provider, we have been serving the Dallas-Fort Worth Area for 31 years. Contact us to find out how we can help your business stay one step ahead with your IT.